An Assessment of the Effectiveness of Pretrained Neural Networks for Malware Detection
Keywords:
Malware, Malware detection, Convolutional Neural Networks, Computer Vision, Transfer LearningAbstract
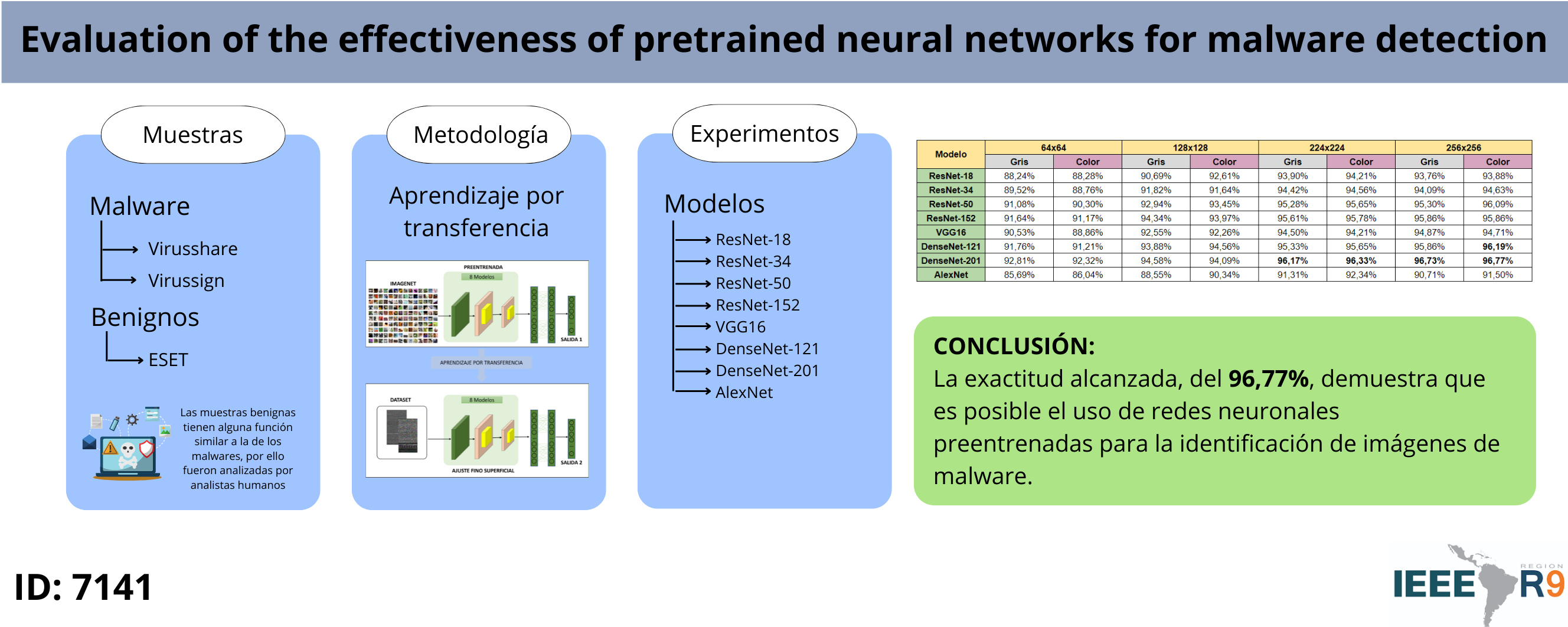
The speed at which malware develops is much faster than analysts are able to analyze it, and it is now a dangerous threat to businesses, critical infrastructure and individuals, forcing anti-virus companies to develop fast and reliable methods for detecting malware. Transfer learning, a deep learning technique, has special abilities such as training speed, lower training dataset size requirements and reduced demand for domain expert knowledge. In this paper, we compared the prediction and model generation performances by using modern convolutional neural networks (Resnet, DenseNet, VGG and AlexNet), which have proven to be successful in the visual classification problem for malware detection. In addition, a dataset containing 14,972 malware samples and 14,500 samples of benign files with some function similar to that possessed by malwares was proposed and used in the study. The best accuracy obtained was 96.35% corresponding to the DenseNet-201 architecture.
Downloads
References
AV-Test, “Malware | av-test.” https://www.av-test.org/es/estadisticas/software-malicioso/, 2022. Accedido el 03/02/2022.
A. I. and K. A., “Android applications scanning: The guide,” in InternationalConference on Computer and Information Sciences (ICCIS),pp. 1–5, Elsevier, 2019.
H. J., R. S.A., G. S., K. S., and D. R., “An efficient densenet-based deeplearning model for malware detection,” Entropy, 2021.
M. V. and A. A., “Malware detection based on code visualization andtwo-level classification,” Information, 2021.
N. M., S. J.H., K. S., R. M., K. M.A., D. R., and B. T., “Hybrid malwareclassification method using segmentation-based fractal texture analysisand deep convolution neural network features,” Appl. Sci., 2020.
Y. Yang, X. Du, Z. Yang, and X. Liu, “Android malware detection basedon structural features of the function call graph,” in Electronics, vol. 10,p. 186, CrossRef, 2021.
M. Nar, A. G. Kakisim, M. N. Yavuz, and I. Sogukpinar, “Analysis andcomparison of disassemblers for opcode based malware analysis,” in2019 4th International Conference on Computer Science and Engineering(UBMK), pp. 17–22, 2019.
S. Alsoghyer and I. Almomani, “Ransomware detection system forandroid applications,” in Electronics, vol. 8, p. 868, CrossRef, 2019.
H. Faris, M. Habib, I. Almomani, M. Eshtay, and I. Aljarah, “Optimizingextreme learning machines using chains of salps for efficient androidransomware detection,” in Appl. Sci., vol. 10, p. 3706, CrossRef, 2020.
J. Jeon, J. Kim, S. Jeon, S. Lee, and Y. Jeong, “Static analysis formalware detection with tensorflow and gpu,” in Advances in ComputerScience and Ubiquitous Computing, pp. 537–546, Springer, 2021.
A. Mohaisen, O. Alrawi, and M. Mohaisen, “Amal: High-fidelity,behavior-based automated malware analysis and classification,” in Comput.Secur., vol. 52, pp. 251–266, CrossRef, 2015.
R. Sihwail, K. Omar, K. Zainol Ariffin, and S. Al Afghani, “Malwaredetection approach based on artifacts in memory image and dynamicanalysis.,” in Appl. Sci., vol. 9, p. 3680, CrossRef, 2019.
S. Roseline, S. Geetha, S. Kadry, and Y. Nam, “Intelligent visionbasedmalware detection and classification using deep random forestparadigm,” in IEEE Access, vol. 8, p. 206303–206324, CrossRef, 2020.
V. Moussas and A. Andreatos, “Malware detection based on code visualizationand two-level classification,” in Information, vol. 12, p. 118,CrossRef, 2021.
M. Nisa, J. Shah, S. Kanwal, M. Raza, M. Khan, R. Damaševiˇcius, and T. Blažauskas, “Hybrid malware classification method usingsegmentation-based fractal texture analysis and deep convolution neuralnetwork features,” in Appl. Sci., vol. 10, p. 4966, CrossRef, 2020.
D. Gibert, C. Mateu, J. Planes, and R. Vicens, “Using convolutionalneural networks for classification of malware represented as images,” inJ. Comput. Virol. Hacking Tech., vol. 15, pp. 15–28, CrossRef, 2019.
S. Jang, S. Li, and Y. Sung, “Fasttext-based local feature visualizationalgorithm for merged image-based malware classification frameworkfor cyber security and cyber defense,” in Mathematics, vol. 8, p. 460,CrossRef, 2020.
D. Vasan, M. Alazab, S. Wassan, H. Naeem, B. Safaei, and Q. Zheng,“Imcfn: Image-based malware classification using fine-tuned convolutionalneural network architecture,” in Comput. Netw., vol. 171, p. 107138,CrossRef, 2020.
G. Xiao, J. Li, Y. Chen, and K. Li, “Malfcs: An effective malwareclassification framework with automated feature extraction based ondeep convolutional neural networks,” in J. Parallel Distrib. Comput.,vol. 141, pp. 49–58, CrossRef, 2020.
S. Saadat and V. Raymond, “Malware classification using cnn-xgboostmodel,” in Artificial Intelligence Techniques for Advanced ComputingApplications, pp. 191–202, Springer, 2021.
D. Vasan, M. Alazab, S. Wassan, B. Safaei, and Q. Zheng, “Image-basedmalware classification using ensemble of cnn architectures (imcec),” inComput. Secur., vol. 92, p. 101748, CrossRef, 2020.
B. Narayanan and V. Davuluru, “Ensemble malware classification systemusing deep neural networks,” in Electronics, vol. 9, p. 721, CrossRef,2020.
S. A. Roseline, A. D. Sasisri, S. Geetha, and C. Balasubramanian, “Towardsefficient malware detection and classification using multilayeredrandom forest ensemble technique,” in 2019 International CarnahanConference on Security Technology (ICCST), pp. 1–6, 2019.
I. Ouahab, M. Bouhorma, A. Boudhir, and L. El Aachak, “Classificationof grayscale malware images using the k-nearest neighbor algorithm,”in Proceedings of the Third International Conference on Smart CityApplications, pp. 1038–1050, Springer, 2019.
H. Naeem, F. Ullah, M. Naeem, S. Khalid, D. Vasan, S. Jabbar, andS. Saeed, “Malware detection in industrial internet of things based onhybrid image visualization and deep learning model,” in Ad Hoc Netw.,vol. 105, p. 102154, CrossRef, 2020.
H. Naeem, B. Guo, M. Naeem, F. Ullah, H. Aldabbas, and M. Javed,“Identification of malicious code variants based on image visualization,”in Comput. Electr. Eng., vol. 76, pp. 1097–1105, CrossRef, 2019.
VirusShare, “Virusshare.com - because sharing is caring.” https://virusshare.com/, 2022. Accedido el 03/02/2022.
VirusSign, “Virussign | malware research & data center, threat intelligence.”https://www.virussign.com/, 2022. Accedido el 03/02/2022.
ESET, “Soluciones antivirus y de seguridad de internet.” https://www.eset.com/ar/, 2022. Accedido el 03/02/2022.
VirusTotal, “Virustotal.” https://www.virustotal.com/, 2022. Accedido el03/02/2022.
L. Nataraj, S. Karthikeyan, G. Jacob, and B. S. Manjunath, “Malwareimages: Visualization and automatic classification,” in Proceedings of the8th International Symposium on Visualization for Cyber Security, VizSec’11, (New York, NY, USA), Association for Computing Machinery,2011.
Y. Lecun, “A theoretical framework for back-propagation,” in Proceedingsof the 1988 Connectionist Models Summer School, CMU,Pittsburg, PA (D. Touretzky, G. Hinton, and T. Sejnowski, eds.), pp. 21–28, Morgan Kaufmann, 1988.
S. Targ, D. Almeida, and K. Lyman, “Resnet in resnet: Generalizingresidual architectures,” arXiv preprint arXiv:1603.08029, 2016.
K. Simonyan and A. Zisserman, “Very deep convolutional networks forlarge-scale image recognition,” arXiv preprint arXiv:1409.1556, 2014.
G. Huang, S. Liu, L. Van der Maaten, and K. Q. Weinberger, “Condensenet:An efficient densenet using learned group convolutions,” inProceedings of the IEEE conference on computer vision and patternrecognition, pp. 2752–2761, 2018.
A. Krizhevsky, I. Sutskever, and G. E. Hinton, “Imagenet classificationwith deep convolutional neural networks,” in Advances in NeuralInformation Processing Systems (F. Pereira, C. Burges, L. Bottou, andK. Weinberger, eds.), vol. 25, Curran Associates, Inc., 2012.
J. Deng, W. Dong, R. Socher, L.-J. Li, K. Li, and L. Fei-Fei, “Imagenet:A large-scale hierarchical image database,” in 2009 IEEE conference oncomputer vision and pattern recognition, pp. 248–255, Ieee, 2009.
A. Krizhevsky, I. Sutskever, and G. E. Hinton, “Imagenet classificationwith deep convolutional neural networks,” Advances in neural informationprocessing systems, vol. 25, 2012.
T. Xiao, L. Liu, K. Li, W. Qin, S. Yu, and Z. Li, “Comparison of transferreddeep neural networks in ultrasonic breast masses discrimination,”BioMed research international, vol. 2018, 2018.
N. Tajbakhsh, J. Y. Shin, S. R. Gurudu, R. T. Hurst, C. B. Kendall, M. B.Gotway, and J. Liang, “Convolutional neural networks for medical imageanalysis: Full training or fine tuning?,” IEEE transactions on medicalimaging, vol. 35, no. 5, pp. 1299–1312, 2016.
M. Izadyyazdanabadi, E. Belykh, M. Mooney, N. Martirosyan, J. Eschbacher,P. Nakaji, M. C. Preul, and Y. Yang, “Convolutional neuralnetworks: Ensemble modeling, fine-tuning and unsupervised semanticlocalization for neurosurgical cle images,” Journal of Visual Communicationand Image Representation, vol. 54, pp. 10–20, 2018.
Fast.ai, “fast.ai - making neural nets uncool again.” https://www.fast.ai/about/, 2022. Accedido el 03/02/2022.