Detection of Facial Spoofing Attacks in Uncontrolled Environments Using ELBP and Color Models
Keywords:
Facial Spoofing, Distance Education, Uncontrolled EnvironmentsAbstract
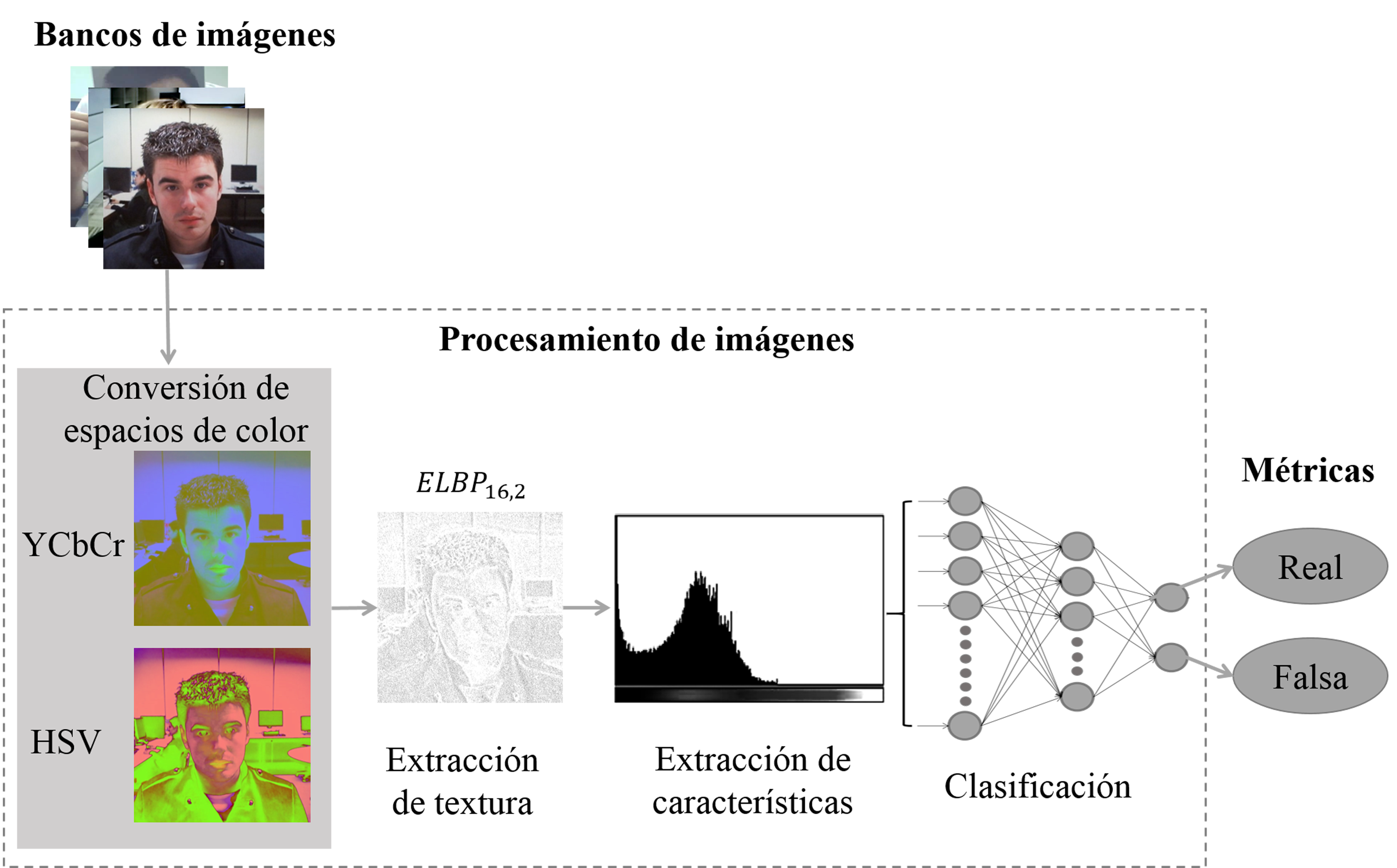
Distance education has become an alternative in teaching derived from the Covid-19 pandemic. However, distance education has led to bad practices for some students. For example, it was detected that some students spoofed the teacher in a class or exam. Therefore, facial biometrics can be used to solve, in real-time, the spoofing problem. However, the solution is not exempt from presentation attacks that undermine the reliability of the systems. Other challenges that must be considered are lighting, resolution, and variable size of the faces, among others. In this paper, we present a methodology to address the problem of facial spoofing attacks. We combine the Extended Local Binary Patterns (ELBP) descriptor and YCbCr, HSV color models to highlight the saturation and illumination of an image. For the experiments, we present a comparison of our proposal against other state-of-the-art methods. We obtain an error of 2.45% with the Half Total Error Rate (HTER) metric in the MSU image bank. The results revealed that for environments where the camera resolutions are not controlled, our proposal provides a feasible solution reducing the costs of acquiring specific hardware
Downloads
References
J. Galbally and S. Marcel, “Biometric antispoofing methods: A survey in face recognition,” IEEE Access, vol. 2, pp. 1530–1552, 2014.
M. Hassaballah and S. Aly, “Face recognition : Challenges, achievements and future directions,” IET Computer Vision, vol. 9, no. 4, pp. 614–626, 2015.
L. Li, P. Correia and A. Hadid, “Face recognition under spoofing attacks: Countermeasures and research directions,” IET Biometrics, vol. 7, no. 1, pp. 3–14, 2017.
S. Angadi and V. Kagawade, “Detection of Face Spoofing using Multiple Texture Descriptors,” in International Conference on Computational Techniques, Electronics and Mechanical Systems (CTEMS), 2019, pp. 151–156.
M. Sajjad, S. Khan, T. Hussain, K. Muhammad, A. Kumar, A. Castiglione, C. Esposito and S. Wook, “CNN-based anti-spoofing two-tier multi-factor authentication system,” Pattern Recognition Letters, vol. 126, pp. 123–131, 2019.
X. Tu, Z. Ma, J. Zhao, G. Du, M. Xie amd J. Feng, “Learning generalizable and identity-discriminative representations for face anti-spoofing,” ACM Transactions on Intelligent Systems and Technology, vol. 11, no. 5, pp. 1-19, 2020.
O. Nikisins, A. George and S. Marcel, “Domain adaptation in multi-channel autoencoder based features for robust face anti-spoofing,” in International Conference on Biometrics (ICB), 2019, pp. 1–8.
I. J. S. Biometrics, “ISO/IEC 30107-1:2016. Information Technology Biometric Presentation Attack Detection,” Part 1 Fram. Int. Organ. Stand., 2016.
Y. Abbas, L. Po, M. Liu, Z. Zou, W. Ou and Y. Zhao, “Face liveness detection using convolutional-features fusion of real and deep network generated face images,” Journal of Visual Communication and Image Representation, vol. 59, pp. 574–582, 2019.
A. Parkin and G. Oleg, “Recognizing multi-modal face spoofing with face recognition networks,” in IEEE Conference on Computer Vision and Pattern Recognition Workshops, 2019, pp. 1617-1623.
Z. Ali and U. Park, “Face spoofing attack detection using spatial frequency and gradient-based descriptor,” KSII Transactions on Internet and Information Systems, vol. 13, no. 2, pp. 892–911, 2019.
A. Mohammadi, S. Bhattacharjee and S. Marcel, “Deeply vulnerable: A study of the robustness of face recognition to presentation attacks,” IET Biometrics, vol. 7, no. 1, pp. 15–26, 2017.
Z. Boulkenafet, J. Komulainen and A. Hadid, “On the generalization of color texture-based face anti-spoofing,” Image and Vision Computing, vol. 77, pp. 1–9, 2018.
J. Määttä, A. Hadid and M. Pietikäinen, “Face spoofing detection from single images using texture and local shape analysis,” IET Biometrics, vol. 1, no. 1, pp. 3–10, 2012.
X. Zhao, Y. Lin and J. Heikkila, “Dynamic texture recognition using volume local binary count patterns with an application to 2d face spoofing detection,” IEEE Transactions on Multimedia, vol. 20, no. 3, pp. 552–566, 2018.
F. Chen, C. Wen, K. Xie, F. Wen, G. Sheng and X. Tang, “Face liveness detection: Fusing colour texture feature and deep feature,” IET Biometrics, vol. 8, no. 6, pp. 369–377, 2019.
R. Raghavendra and R. Sanjeev, “A novel feature descriptor for face anti-spoofing using texture based method,” Cybernetics and Information Technologies, vol. 20, no. 3, pp. 159–176, 2020.
X. Shu, H. Tang and S. Huang, “Face spoofing detection based on chromatic ED-LBP texture feature,” Multimedia Systems, vol. 27, pp. 161–176, 2021.
P. Chan, W. Liu, D. Chen, D. Yeung, F. Zhang, X. Wang and C. Hsu, “Face liveness detection using a flash against 2d spoofing attack,” IEEE Transactions on Information Forensics and Security, vol. 13, no. 2, pp. 521–534, 2018.
A. Kartika, I. Kusuma, T. Agung, B. Wirayuda and K. Nur, “Image spoofing detection using local binary pattern and local binary pattern variance,” International Journal on Information and Communication Technology (IJoICT), vol. 4, no. 2, pp. 11–18, 2019.
L. Song and H. Ma, “Face liveliness detection based on texture and color features,” in 2019 IEEE 4th International Conference on Cloud Computing and Big Data Analysis, 2019, pp. 418–422.
A. Tsitiridis, C. Conde, B. Ayllon and E. Cabello, “Bio-inspired presentation attack detection for face biometrics,” Frontiers in Computational Neuroscience, vol. 13, pp. 1–17, 2019.
G. Simanjuntak, K. Ramadhani, and A. Arifianto, “Face spoofing detection using color distortion features and principal component analysis,” in 7th International Conference on Information and Communication Technology (ICoICT), 2019, pp. 1-5.
D. Arini, K. Ramadhani and F. Sthevanie, “Detection of face spoofing using low-level features and shape analysis,” Journal of Physics, vol. 1192, pp. 012002, 2019.
T. Edmunds and A. Caplier, “Motion-based countermeasure against photo and video spoofing attacks in face recognition,” Journal of Visual Communication and Image Representation, vol. 50, pp. 314–332, 2018.
B. Ahirwal, M. Khadtare and R. Mehta, “FPGA based system for Color Space Transformation RGB to YIQ and YCbCr,” in 2007 International Conference on Intelligent and Advanced Systems (ICIAS), 2007, pp. 1345–1349, 2007.
G. Saravanan, G. Yamuna and S. Nandhini, “Real time implementation of RGB to HSV/HSI/HSL and its reverse color space models,” in 2016 International Conference on Communication and Signal Processing (ICCSP), 2016, pp. 462–466.
L. Liu, S. Lao, P. Fieguth, Y. Guo, X. Wang and M. Pietikäinen, “Median robust extended local binary pattern for texture classification,” IEEE Transactions on Image Processing, vol. 25, no. 3, pp. 1368–1381, 2016.
M. Chris, M. Pavel, M. Timo and A. Jan, “Mobile biometry (mobio) face and speaker verification evaluation,” in International Conference on Pattern Recognition (ICPR), 2010, pp. 1-28.
B. Peixoto, C. Michelassi and A. Rocha, “Face liveness detection under bad illumination conditions,” in 18th IEEE International Conference on Image Processing, 2011, pp. 3557–3560.
A. Anjos and S. Marcel, “Counter-measures to photo attacks in face recognition: a public database and a baseline,” in 2011 International Joint Conference on Biometrics (IJCB), 2011, pp. 1–7.
G. Kim, S. Eum, J. Suhr, D. Kim, K. Park, and J. Kim, “Face liveness detection based on texture and frequency analyses,” in 5th IAPR International Conference on Biometrics (ICB), 2012, pp. 1–6.
A. Pinto, W. Schwartz, H. Pedrini and A. Rocha, “Using visual rhythms for detecting video-based facial spoof attacks,” IEEE Transactions on Information Forensics and Security, vol. 10, no. 5, pp. 1025–1038, 2015.
A. Costa-pazo, S. Bhattacharjee, E. Vazquez-Fernandez, and S. Marcel, “The replay-mobile face presentation-attack database,” in 2016 International Conference of the Biometrics Special Interest Group (BIOSIG) , 2016, pp. 1–7.
D. Wen, H. Han, and A. K. Jain, “Face spoof detection with image distortion analysis,” I IEEE Transactions on Information Forensics and Security, vol. 10, no. 4, pp. 746–761, 2015.
Z. Zhang, J. Yan, S. Liu, Z. Lei, D. Yi, and S. Li, “A face antispoofing database with diverse attacks,” in 2012 5th IAPR International Conference on Biometrics (ICB), 2012, pp. 26–31.
T. Ojala, M. Pietikäinen, and T. Mäenpää, “Multiresolution gray-scale and rotation invariant texture classification with local binary patterns,” IEEE Transactions on Pattern Analysis and Machine Intelligence, vol. 24, no. 7, pp. 971–987, 2002.
A. Goshtasby, Image Registration: Principles, Tools and Methods, Springer, 1st Edition, 2012.
S. Bengio and J. Mariéthoz, “A statistical significance test for person authentication,” in Proceedings of Odyssey 2004: The Speaker and Language Recognition Workshop, 2004, pp. 1-8.
D. Basso, “Propuesta de métricas para proyectos de explotación de información,” Revista Latinoamericana de Ingeniería de Software, vol. 2, no. 4, pp. 157-218, 2015.