Hardware Implementation of Authenticated Ciphers for Embedded Systems
Keywords:
Authentication, Ciphers, Cryptography, Embedded Systems Security, FPGAAbstract
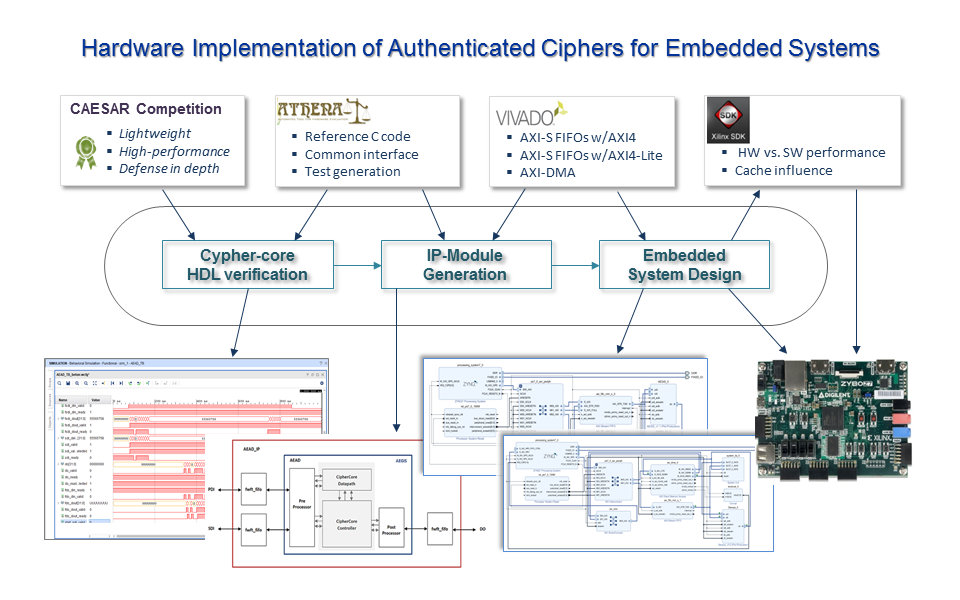
The demand for embedded systems in applications that handle critical or private information has strongly focused designers' attention on the security aspects of this kind of system. Using the C programs and HDL descriptions available in the repositories of the CAESAR Competition and the ATHENa Project, this work presents a design flow that eases the development and evaluation of different solutions for the hardware implementation of authenticated ciphers and their incorporation as accelerating peripherals in embedded systems for different application cases. Three ciphers, finalists in the different categories established in the contest, have been analyzed, although the described approaches can be applied to any of the proposals submitted to the CAESAR Competition. A Zybo-Z7 development board that incorporates a Zynq-7000 device from Xilinx, which combines programmable logic from the FPGAs of the 7-Series with a dual-core Cortex-A9 ARM processing system, has been used as hardware platform in all the designs. The Vivado environment has been employed to perform the different stages of synthesis and verification necessary to carry out the implementation of the cipher, its conversion into an IP module, and its integration in an embedded system using different interconnection schemes that allow establishing cost/performance tradeoffs for different applications.
Downloads
References
J. R. Almeida, J. B. Camargo, P. S. Cugnasca, “Safety and Security in Critical Applications and in Information Systems - a Comparative Study,” IEEE Latin America Transactions, vol. 11, no. 4, pp. 1127-1133, June 2013, 10.1109/TLA.2013.6601759.
CAESAR Competition for Authenticated Encryption: Security, Applicability, and Robustness, 2012. [Online].
Disponible: http://competitions.cr.yp.to/caesar.html
J. Daemen, V. Rijmen, The Design of Rijndael: AES - The Advanced Encryption Standard, Springer Science & Business Media, 2013.
Z. Zhang, M. C. Y. Cho, C. Wang, C. Hsu, C. Chen, S. Shieh, “IoT Security: Ongoing Challenges and Research Opportunities,” in Proc. IEEE 7th International Conference on Service-Oriented Computing and Applications, Matsue, 2014, 10.1109/SOCA.2014.58.
N. Jazdi, “Cyber physical systems in the context of Industry 4.0,” in Proc. 2014 IEEE International Conference on Automation, Quality and Testing, Robotics, Cluj-Napoca, 2014, 10.1109/AQTR.2014.6857843.
L. Thames, D. Schaefer, Cybersecurity for Industry 4.0. Springer Series in Advanced Manufacturing. Springer, 2017. 10.1007/978-3-319-50660-9.
B. Zhou, M. Egele, A. Joshi, “High-performance low-energy imple-mentation of cryptographic algorithms on a programmable SoC for IoT devices,” in Proc. 2017 IEEE High Performance Extreme Computing Conference, Waltham, 2017, 10.1109/HPEC.2017.8091062.
R Cowart, D Coe, J Kulick,, A Milenković, “An Implementation and Experimental Evaluation of Hardware Accelerated Ciphers in All-Programmable SoCs,” in Proc. of the SouthEast Conference. ACM, Kennesaw 2017, 10.1145/3077286.3077297.
N. Jacob et al., “Securing FPGA SoC configurations independent of their manufacturers,” In Proc. 30th IEEE International System-on-Chip Conference, Munich, 2017, 10.1109/SOCC.2017.8226019.
A. Silitonga, Z. Jiang, N. Khan, J. Becker, “Reconfigurable Module of Multi-mode AES Cryptographic Algorithms for AP SoCs,” in Proc, 2019 IEEE Nordic Circuits and Systems Conference, Helsinki, 2019, 10.1109/NORCHIP.2019.8906923.
I. G. Agramont, H. Calderón, “Evaluation of Cryptographic Algorithms over an All Programmable SoC (AP SoC) Device,” Journal on Systemics, Cybernetics and Informatics, vol. 15, no. 2, pp. 84-91, 2017.
National Institute of Standards and Technology “FIPS-46:(1979): Data Encryption Standard (DES),” Revisión 46-3 (1999) disponible en: http://csrc.nist.gov/publications/fips/fips46-3/fips46-3.pdf.
R. Rivest, A. Shamir, L. Adleman. “A Method for Obtaining Digital Signatures and Public-Key Cryptosystems,” Communications of the ACM, vol. 21 no. 2, pp.120–126. 1978, 10.1145/359340.359342.
M. Grassl, B. Langenberg, M. Roetteler, R. Steinwandt, “Applying Grover’s Algorithm to AES: Quantum Resource Estimates,” in: Takagi T. (eds) Post-Quantum Cryptography 2016. Lecture Notes in Computer Science, vol 9606. Springer, Cham. 10.1007/978-3-319-29360-8_3.
J. Xie, K. Basu, K. Gaj, U. Guin “Special Session: The Recent Advance in Hardware Implementation of Post-Quantum Cryptography,” in Proc. 2020 IEEE 38th VLSI Test Symposium, San Diego, 2020, pp. 1-10, 10.1109/VTS48691.2020.9107585.
GMU Source Code of Round 3 & Round 2 CAESAR Candidates, AES-GCM, AES, and Keccak Permutation F, [Online]. Disponible: https://cryptography.gmu.edu/athena/index.php?id=CAESAR_source_codes.
K. Gaj, J.-P. Kaps, V. Amirineni, M. Rogawski, E. Homsirikamol, B. Y. Brewster, “ATHENa – automated tool for hardware evaluation: Toward fair and comprehensive benchmarking of cryptographic hardware using FPGAs,” in Proc. 20th International Conference on Field Programmable Logic and Applications, 2010. pp. 414–421.
C. Dobraunig, M. Eichlseder, F Mendel, M. Schläffer, “Ascon v1.2, Submission to the CAESAR Competition,” Sep. 2016. [Online].
Disponible: http://competitions.cr.yp.to/round3/asconv12.pdf.
H. Wu, “ACORN: A Lightweight Authenticated Cipher (v3),” Sep. 2016. [Online].
Disponible: https://competitions.cr.yp.to/round3/acornv3.pdf.
H. Wu, B. Preneel, “AEGIS: A Fast Authenticated Encryption Algorithm (v1.1),” Sep. 2016. [Online].
Disponible: http://competitions.cr.yp.to/round3/aegisv11.pdf.
T. Krovetz, P. Rogaway, “OCB (v1.1),” Sep. 2016. [Online].
Disponible: http://competitions.cr.yp.to/round3/ocbv11.pdf.
J. Jean, I. Nikolic, T. Peyrin, Y. Seurin, “Deoxys v1.41,” Sep. 2016. [Online]. Disp.: http://competitions.cr.yp.to/round3/deoxysv141.pdf.
E. Andreeva el al., “COLM v1,” Sep. 2016, [Online].
Disponible: http://competitions.cr.yp.to/round3/colmv1.pdf.
Digilent, “Zybo Z7: Zynq-7000 ARM/FPGA SoC Development Board,” [Online].
Disponible: https://reference.digilentinc.com/reference/programmable-logic/zybo-z7/start
George Mason University, “ATHENA: Automated Tool for Hardware EvaluatioN,” 2010. [Online]. Disponible: https://cryptography.gmu.edu/athena/index.php?id=ATHENa
E. Homsirikamol, W. Diehl, A. Ferozpuri, F. Farahmand, P. Yalla, J. P. Kaps, K. Gaj, “CAESAR Hardware API,” Cryptology ePrint Archive 2016/626, 2016. [Online].
Disponible: http://eprint.iacr.org/2016/626.pdf
George Mason University: “Development Package for Hardware Implementations Compliant with the CAESAR Hardware API, v2.0,” 2017. [Online]. Disponible:
https://cryptography.gmu.edu/athena/index.php?id=CAESAR
E. Homsirikamol, P. Yalla, F. Farahmand, W. Diehl, A. Ferozpuri, J.-P. Kaps, K. Gaj, “Implementer’s Guide to Hardware Implementations Compliant with the CAESAR Hardware API,” George Mason University, Fairfax, VA, GMU Report, 2016.
Cryptographic Engineering Research Group at GMU, “GMU ATHENa Database of Results,” Dec. 2017. [Online]. Available: https://cryptography.gmu.edu/athenadb/fpga_auth_cipher/rankings_view
Cryptographic Engineering Research Group at GMU, “Hardware Benchmarking of CAESAR Candidates,” 2019. [Online]. Available: https://cryptography.gmu.edu/athena/index.php?id=CAESAR.
F. Farahmand, W. Diehl, A. Abdulgadir, J.-P. Kaps, K. Gaj, “Improved Lightweight Implementations of CAESAR Authenticated Ciphers,” in Proc. 2018 IEEE 26th Annual International Symposium on Field-Programmable Custom Computing Machines, Boulder, CO, Apr. 2018.
W. Diehl, F. Farahmand, A. Abdulgadir, J. P. Kaps, K. Gaj, “Face-off between the CAESAR Lightweight Finalists: ACORN vs. Ascon,” In Proc. International Conference on Field Programmable Technology (ICFPT), Naha, Japan. Dec. 2018.
M. Tempelmeier, F. De Santis, G. Sigl, J.-P. Kaps, “The CAESAR-API in the real world — Towards a fair evaluation of hardware CAESAR candidates,” in Proc. 2018 IEEE International Symposium on Hardware Oriented Security and Trust, Washington, DC, Apr. 2018.
Xilinx, “Vivado Design Suite User Guide v. 2018.2, ” Jul. 2018. [Online]. Disponible: https://www.xilinx.com/support/documentation/sw_manuals/xilinx2018_2/ug973-vivado-release-notes-install-license.pdf
Xilinx, “Xilinx Software Development Kit (XSDK) 2018.2. ” [Online]. Disponible: https://www.xilinx.com/products/design-tools/embedded-software/sdk.html