An Audio Encryption Scheme Based on Empirical Mode Decomposition and 2D Cosine Logistic Map
Keywords:
Encryption, Audio encryption, Security, Chaotic map, 2D chaotic map, Empirical Mode DecompositionAbstract
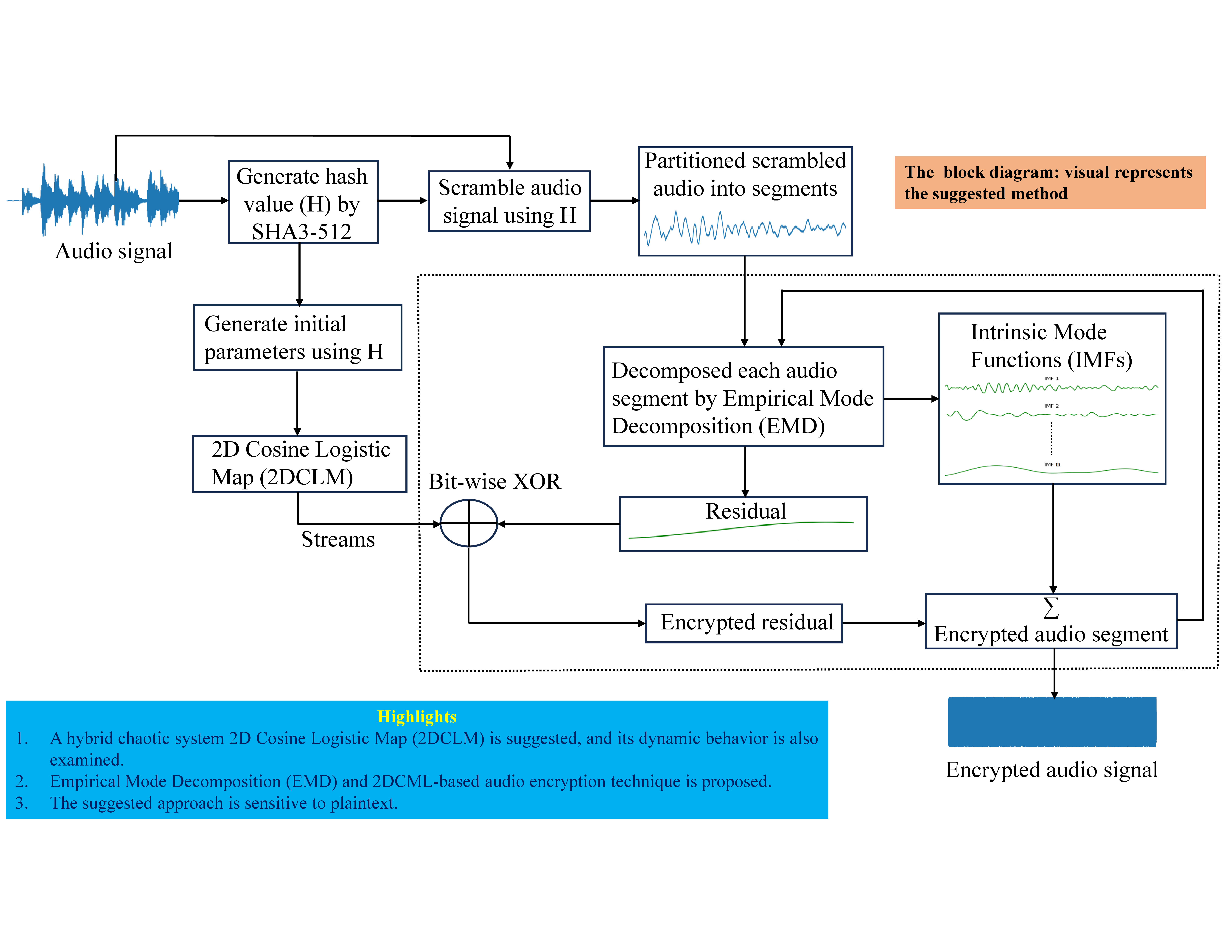
In this work, we have proposed an audio encryption method. The proposed method is audio signal sensitive as the hash value of the given signal is computed using SHA3-512, which returns a significantly large key of size 512-bit. This key is used to set the different parameters. This work suggests a 2D Cosine Logistic Map (2DCLM) by fusing the Cosine map with the Logistic map. The proposed 2DCLM functions well under chaos. The given audio signal is scrambled with the help of the hash value. The scrambled signal is decomposed by Empirical Mode Decomposition (EMD); before using the EMD the signal is segmented into a 2D signal to reduce the time complexity of the EMD method. The residuals given by EMD and the stream generated by 2DCLM are XOR-ed to encrypt the signal. Finally, the 2D encrypted signal is transformed into a 1D encrypted audio signal. The efficacy of the present method is evaluated with the help of different audio streams. The findings of the simulation and comparison indicate that the suggested technique may deliver effective encryption results while thwarting cryptographic assaults.
Downloads
References
H. Aziz, S. M. M. Gilani, I. Hussain, A. K. Janjua, and S. Khurram, “A noise-tolerant audio encryption framework designed by the application of s8 symmetric group and chaotic systems,” Mathematical Problems in Engineering, vol. 2021, pp. 1–15, 2021. https://doi.org/10.1155/2021/5554707.
E. A. Albahrani, T. K. Alshekly, and S. H. Lafta, “A review on audio encryption algorithms using chaos maps-based techniques,” Journal of Cyber Security and Mobility, pp. 53–82, 2022. https://doi.org/10.13052/jcsm2245-1439.1113.
M. Karmani, N. Benhadjyoussef, B. Hamdi, and M. Machhout, “The sha3-512 cryptographic hash algorithm analysis and implementation on the leon3 processor,” https://doi.org/10.14445/22315381/IJETT-V69I6P210
C. Albin, D. Narayan, R. Varu, and V. Thanikaiselvan, “Dwt based audio encryption scheme,” in 2018 second international conference on electronics, communication and aerospace technology (ICECA), pp. 920–924, IEEE, 2018. https://doi.org/10.1109/ICECA.2018.8474602.
H. Kakaei Kate, J. Razmara, and A. Isazadeh, “A novel fast and secure approach for voice encryption based on dna computing,” 3D Research, vol. 9, pp. 1–11, 2018. https://doi.org/10.1007/s13319-018-0167-x.
P. K. Naskar, S. Paul, D. Nandy, and A. Chaudhuri, “Dna encoding and channel shuffling for secured encryption of audio data, ” Multimedia Tools and Applications, vol. 78, pp. 25019–25042, 2019. https://doi.org/10.1007/s11042-019-7696-z.
X. Wang and Y. Su, “An audio encryption algorithm based on dna coding and chaotic system,” IEEE Access, vol. 8, pp. 9260–9270, 2019. https://doi.org/10.1109/ACCESS.2019.2963329
D. Shah, T. Shah, and S. S. Jamal, “Digital audio signals encryption by mobius transformation and hénon map,” Multimedia systems, vol. 26, pp. 235–245, 2020. https://doi.org/10.1007/s00530-019-00640-w.
F. Farsana, V. Devi, and K. Gopakumar, “An audio encryption scheme based on fast walsh hadamard transform and mixed chaotic keystreams, ”Applied Computing and Informatics, no. ahead-of-print, 2020. https://doi.org/10.1016/j.aci.2019.10.001.
S. El-Zoghdy, H. S. El-sayed, and O. S. Faragallah, “Transmission of chaotic-based encrypted audio through ofdm,” Wireless Personal Communications, vol. 113, pp. 241–261, 2020. https://doi.org/10.1007/
s11277-020-07187-4.
G. Kaur, K. Singh, and H. S. Gill, “Chaos-based joint speech encryption scheme using sha-1,” Multimedia tools and applications, vol. 80, pp. 10927–10947, 2021. https://doi.org/10.1007/s11042-020-10223-x
W. Dai, X. Xu, X. Song, and G. Li, “Audio encryption algorithm based on chen memristor chaotic system,” Symmetry, vol. 14, no. 1, p. 17, 2021. https://doi.org/10.3390/sym14010017
S. Adhikari and S. Karforma, “A novel audio encryption method using henon–tent chaotic pseudo random number sequence,” International Journal of Information Technology, vol. 13, no. 4, pp. 1463–1471, 2021. https://doi.org/10.1007/s41870-021-00714-x
A. H. Khaleel and I. Q. Abduljaleel, “A novel technique for speech encryption based on k-means clustering and quantum chaotic map, ”Bulletin of Electrical Engineering and Informatics, vol. 10, no. 1,
pp. 160–170, 2021. https://doi.org/10.11591/eei.v10i1.2405.
Nasreen and P. Muthukumar, “Secure audio signal encryption based on triple compound-combination synchronization of fractional-order dynamical systems,” International Journal of Dynamics and Control, vol. 10, no. 6, pp. 2053–2071, 2022. https://doi.org/10.1007/s40435-022-00942-4.
O. M. Al-Hazaimeh, A. A. Abu-Ein, K. M. Nahar, and I. S. Al-Qasrawi, “Chaotic elliptic map for speech encryption,” Indonesian Journal of Electrical Engineering and Computer Science, vol. 25, no. 2, pp. 1103–
, 2022. https://doi.org/10.11591/ijeecs.v25.i2.pp1103-1114.
R. Wu, S. Gao, X. Wang, S. Liu, Q. Li, U. Erkan, and X. Tang, “Aeancs: An audio encryption algorithm based on a nested chaotic system, ”Chaos, Solitons & Fractals, vol. 165, p. 112770, 2022. https://doi.org/10.1016/j.chaos.2022.112770.
A. Kumar and M. Dua, “Audio encryption using two chaotic map based dynamic diffusion and double dna encoding,” Applied Acoustics, vol. 203, p. 109196, 2023. https://doi.org/10.1016/j.apacoust.2022.
L. E. Bassham III, A. L. Rukhin, J. Soto, J. R. Nechvatal, M. E. Smid, E. B. Barker, S. D. Leigh, M. Levenson, M. Vangel, D. L. Banks, et al., Sp 800-22 rev. 1a. a statistical test suite for random and pseudorandom
number generators for cryptographic applications. National Institute of Standards & Technology, 2010. https://doi.org/10.6028/NIST.SP.800-22r1a.
G. Li, X. Xu, and H. Zhong, “A image encryption algorithm based on coexisting multi-attractors in a spherical chaotic system,” Multimedia Tools and Applications, vol. 81, no. 22, pp. 32005–32031, 2022. https://doi.org/10.1007/s11042-022-12853-9.
N. E. Huang, Z. Shen, S. R. Long, M. C. Wu, H. H. Shih, Q. Zheng, N. C. Yen, C. C. Tung, and H. H. Liu, “The empirical mode decomposition and the hilbert spectrum for nonlinear and non-stationary time series
analysis,” Proceedings of the Royal Society of London. Series A: mathematical, physical and engineering sciences, vol. 454, no. 1971, pp. 903–995, 1998. https://doi.org/10.1098/rspa.1998.0193.
H. Ge, G. Chen, H. Yu, H. Chen, and F. An, “Theoretical analysis of empirical mode decomposition,” Symmetry, vol. 10, no. 11, p. 623, 2018. https://doi.org/10.3390/sym10110623.
https://www2.cs.uic.edu/~i101/SoundFiles/.
G. Alvarez and S. Li, “Cryptographic requirements for chaotic secure communications,” arXiv preprint nlin/0311039, 2003. https://doi.org/10.1142/S0218127406015970.
E. M. Guizzo, The essential message: Claude Shannon and the making of information theory. PhD thesis, Massachusetts Institute of Technology, 2003. https://doi.org/1721.1/39429.
P. Sathiyamurthi and S. Ramakrishnan, “Speech encryption using hybridhyper chaotic system and binary masking technique,” Multimedia Tools and Applications, vol. 81, no. 5, pp. 6331–6349, 2022. https://doi.org/10.1007/s11042-021-11757-4.
D. Shah, T. Shah, M. M. Hazzazi, M. I. Haider, A. Aljaedi, and I. Hussain, “An efficient audio encryption scheme based on finite fields,” IEEE Access, vol. 9, pp. 144385–144394, 2021. https://doi.org/10.1109/
ACCESS.2021.3119515.
R. I. Abdelfatah, “Audio encryption scheme using self-adaptive bit scrambling and two multi chaotic-based dynamic dna computations,” IEEE Access, vol. 8, pp. 69894–69907, 2020. https://doi.org/10.1109/
ACCESS.2020.2987197.