Remainder with Threshold Substitution Data Hiding Scheme: Counterexamples and Modification
Keywords:
Data hiding scheme, Remainder with threshold substitution, Cover Image, Pixel, Secret Embedding, Secret ExtractionAbstract
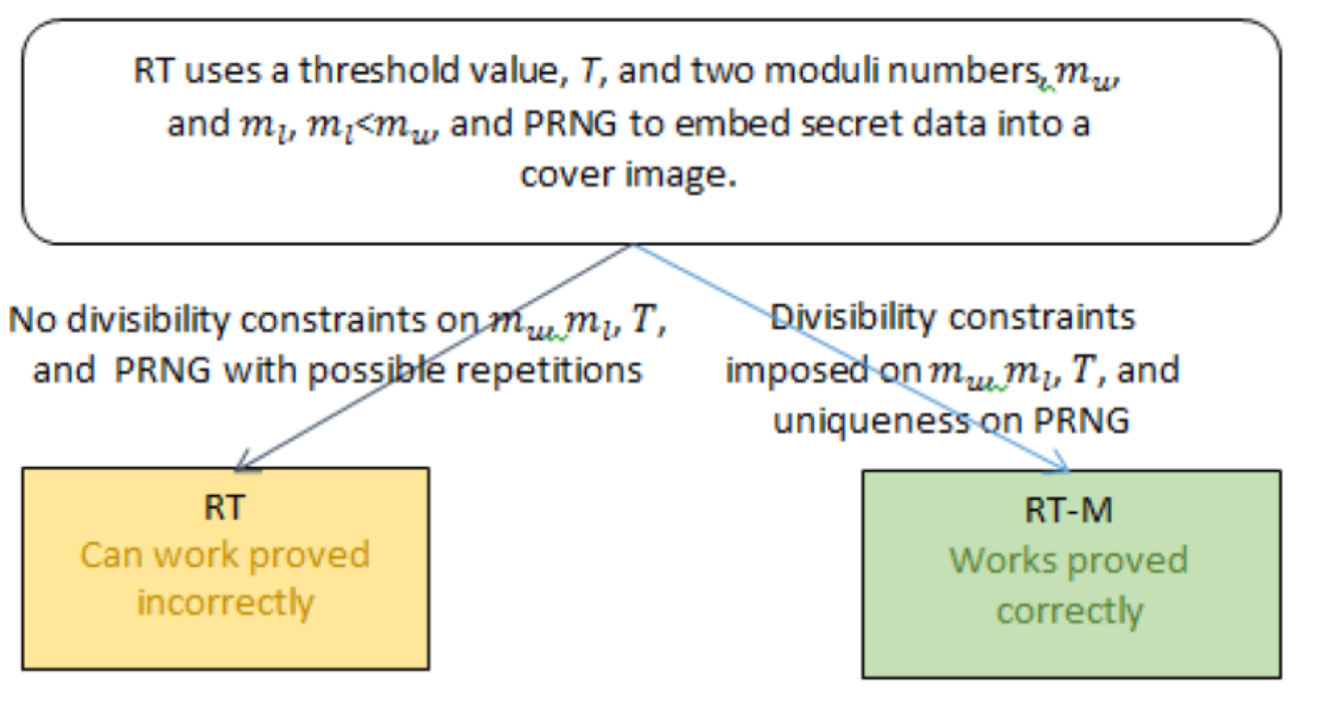
A well-known data hiding scheme, Remainder with Threshold substitution (RT), is analyzed. RT uses a threshold value, T, and two moduli numbers, m_u, and m_l, m_l<m_u, to embed secret data into a cover image. RT does not impose any divisibility constraints on the selection of the parameters, T, m_u, and m_l, and its correctness (i.e., the data extracted are always the same as the data embedded) is not proved. By counterexamples constructing, we show that RT works for them incorrectly. Also, RT scheme uses pseudo-random number generator (PRNG) to define a pixel for embedding of the next secret bit portion. PRNG can produce repeated values leading to the repeated embedding into the same pixel, thus overwriting previously embedded secret and preventing its correct extraction. We modify RT scheme (by imposing divisibility constraints on the threshold, moduli values, and PRNG), and prove correctness of the modification. Note that in the reported experiments on RT, its parameters used, T=160, and (m_l, m_u) from {(4, 8), (16, 32)}, exactly satisfy our constraints, and, thus, the scheme may be correct for such settings.
Downloads
References
Wang SJ (2005) Steganography of capacity required using modulo operator for embedding secret image. Applied Mathematics and Computation 164:99–116
Chang CC, Chan CS, Fan YH (2006) Image hiding scheme with modulus function and dynamic programming strategy on partitioned pixels. Pattern Recognition 39(6):1155-1167
Chen WY (2007) Color image steganography scheme using set partitioning in hierarchical trees coding, digital Fourier transform and adaptive phase modulation. Applied Mathematics and Computation 185(1):432-448
Lin SJ, Lin JC (2007) VCPSS: A two-in-one two-decoding-options image sharing method combining visual cryptography (VC) and polynomial-style sharing (PSS) approaches. Pattern Recognition 40(12):3652-3666
Wang CM, Wu NI, Tsai CS, Hwang MS (2008) A high quality steganographic method with pixel-value differencing and modulus. Journal of Systems and Software 81(1):150-158
Yang CH (2008) Inverted pattern approach to improve image quality of information hiding by LSB substitution. Pattern Recognition 41(8):2674-2683
Chang YJ, Wang RZ, Lin JC (2008) Hiding images using modified search-order coding and modulus function. International Journal of Pattern Recognition and Artificial Intelligence 22(6):1215-1240
Chang CC, Hsiehb YP, Lina CH (2008) Sharing secrets in stego images with authentication. Pattern Recognition 41(10):3130-3137
Hsieha YP, Changa CC, Liua LJ (2008) A two-codebook combination and three-phase block matching based image-hiding scheme with high embedding capacity. Pattern Recognition 41(10):3104-3113
Lin IC, Lin YB, Wang CM (2009) Hiding data in spatial domain images with distortion tolerance. Computer Standards & Interfaces 31(2):458-464
Eslami Z, Razzaghi SH, Ahmadabadi JZ (2010) Secret image sharing based on cellular automata and steganography. Pattern Recognition 43(1):397-404
Chang CC, Hsieh YP (2010) A chaotic map-based adaptive variable-size LSB method with pixel-value differencing and modulus. Image Science Journal 58(1):49-60
Chen LST, Lin SJ, Lin JC (2010) Reversible JPEG-based hiding method with high hiding-ratio. International Journal of Pattern recognition and Artificial Intelligence 24(3):433-456
Lou DC, Wu NI, Wang CM et al (2010) A novel adaptive steganography based on local complexity and human vision sensitivity. Journal of Systems and Software 83(7):1236-1248
Yang CH, Weng CY, Wang SJ et al (2010) Varied PVD+LSB evading detection programs to spatial domain in data embedding systems. Journal of Systems and Software 83(10):1635-1643
Wu NI, Fu KC, Wang CM (2010) A novel data hiding method for gray scale images based on pixel-value differencing and modulus function. Journal of Internet technology 11(7):1071-1081
Liao X, Wen QY, Zhang J (2011) A steganographic method for digital images with four-pixel differencing and modified LSB substitution. Journal of Visual Communication and Image Representation 22(1):1-8
Lin PY, Lee JS, Chang CC (2011) Protecting the content integrity of digital imagery with fidelity preservation. ACM Transaction on Multimedia Computing Communications and Applications 7(3):1-20
Lin CC (2011) An information hiding scheme with minimal image distortion. Computer Standards & Interfaces 33(5):477-484
Lou DC, Hu CH (2012) LSB steganographic method based on reversible histogram transformation function for resisting statistical steganalysis. Information Sciences 188:346-358
Liu S, Chen Y, Jiang F et al (2012) A New Steganographic method based on equivalence class partition. Journal of Computational and Theoretical Nanoscience 9(10):1757-1765
Sajasi S, Moghadam AME (2015) An adaptive image steganographic scheme based on noise visibility function and an optimal chaotic based encryption method. Applied Soft Computing 30:375-389
Jana B (2016) High payload reversible data hiding scheme using weighted matrix. Optik 127(6):3347-3358
Xu WL, Chang CC, Chen TS et al (2016) An improved least-significant-bit substitution method using the modulo three strategy. Displays 42:36-42
Liu L, Chang CC, Wang A (2017) Data hiding based on extended turtle shell matrix construction method. Multimedia Tools and Applications 76(10):12233-12250
Wu NI, Hwang MS (2017) A novel LSB data hiding scheme with the lowest distortion. The Imaging Science Journal 65(6):371-378
Liu L, Chang CC, Anhong W (2017) Data hiding based on extended turtle shell matrix construction method. Multimedia Tools and Applications 76(10):12233-12250
Jana B (2018) Reversible data hiding scheme using sub-sampled image exploiting Lagrange’s interpolating polynomial. Multimedia Tools Applications 77:8805–8821
Datta B, Roy S, S. Roy, Bandyopadhyay SM (2019) Multi-bit robust image steganography based on modular arithmetic. Multimedia Tools Applications 78(2):1511-1546
Nashat D, Mamdouh L (2019) An efficient steganographic technique for hiding data. Journal of the Egyptian Mathematical Society 27(1):1-4
Zenati A, Ouarda W, Alimi AM (2020) SSDIS-BEM: A New Signature Steganography Document Image System based on Beta Elliptic Modeling. Engineering Science and Technology, an International Journal 23(3):470-82
Zenati A, Ouarda W, Alimi AM (2021) A new digital steganography system based on hiding online signature within document image data in YUV color space. Multimedia Tools and Applications 80(12):18653-7
Ping P, Yang X, Zhang X, Mao Y, Khalid H (2022) Generating visually secure encrypted images by partial block pairing-substitution and semi-tensor product compressed sensing. Digital Signal Processing 120. https://doi.org/10.1016/j.dsp.2021.103263
Ko HJ, Huang CT, Tseng H W. Wang SJ (2022) Efficient Cost-Reduced With High-Quality Image of Imperceptible Steganography Using Modulo and Magic Cube. IEEE Access 10:67686-67693. doi: 10.1109/ACCESS.2022.3185120
Hu Y, Li X, Ma J (2022) A Novel LSB Matching Algorithm Based on Information Pre-Processing. Mathematics 2022, 10, 8.
https://doi.org/10.3390/math10010008.
Chan C-K, Cheng LM (2004) Hiding Data in Images by Simple LSB Substitution. Pattern Recognition 37, 469-474, doi:10.1016/j.patcog.2003.08.007