Transfer learning for face anti-spoofing detection
Keywords:
Face anti-spoofing, Transfer Learning, Deep Learning, VGG16Abstract
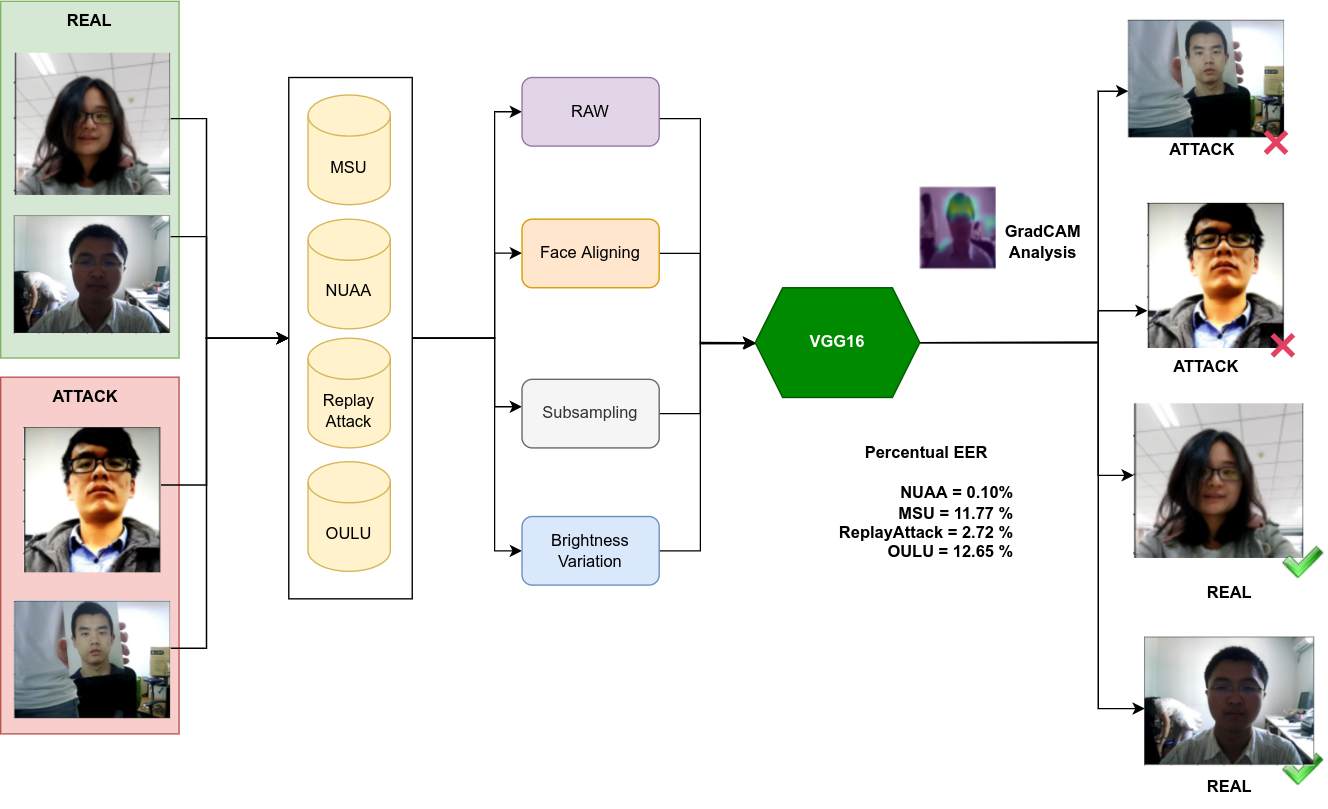
In recent years, the demand for facial biometric authentication services has increased dramatically. Also, the efforts to cheat this type of system have become more common. In this paper, we propose a single shot CNN-based solution for the face anti-spoofing problem. We trained a deep learning model using transfer learning from a pre-trained VGG16 model. After some pre-processing we rely solely on the network to classify an image. We evaluate several implications of the preprocessing of data, investigate the implications of different amounts of background included in the picture, and the effect of data subsampling. Additionally, we analyze what happens when we sub-sample the training data. We evaluate our results in four publicly available datasets, drawing some insights on the results by using the Grad-CAM algorithm. Our approach is competitive when compared with similar methods. Moreover, we achieved our results while training with a fraction of the original datasets, enforcing that experiments can be run much quicker without sacrificing accuracy.
Downloads
References
World Health Organization, “What you need to know about the new omicron covid-19 variant,” 2021. [Online; accessed 09-December-2021].
World Health Organization, “Listings of who’s response to covid-19,” 2021. [Online; accessed 09-December-2021].
Centers of Disease Control and Prevention, “How to protect yourself others,” 2021. [Online; accessed 09-December-2021].
M. Gomez-Barrero, P. Drozdowski, C. Rathgeb, J. Patino, M. Todisco, A. Nautsch, N. Damer, J. Priesnitz, N. Evans, and C. Busch, “Biometrics in the era of covid-19: Challenges and opportunities,” arXiv preprint
arXiv:2102.09258, 2021.
Y. A. U. Rehman, L. M. Po, and M. Liu, “Deep learning for face antispoofing: An end-to-end approach,” in 2017 Signal Processing: Algorithms, Architectures, Arrangements, and Applications (SPA), pp. 195–200, IEEE, 2017.
S. Marcel, M. S. Nixon, J. Fierrez, and N. Evans, Handbook of biometric anti-spoofing: Presentation attack detection. Springer, 2019.
S. Kumar, S. Singh, and J. Kumar, “A comparative study on face spoofing attacks,” in 2017 International Conference on Computing,
Communication and Automation (ICCCA), pp. 1104–1108, IEEE, 2017.
L. Sun, W. Huang, and M. Wu, “Tir/vis correlation for liveness detection in face recognition,” in International Conference on Computer Analysis of Images and Patterns, pp. 114–121, Springer, 2011.
Z. Zhang, D. Yi, Z. Lei, and S. Z. Li, “Face liveness detection by learning multispectral reflectance distributions,” in 2011 IEEE International Conference on Automatic Face & Gesture Recognition (FG), pp. 436–441, IEEE, 2011.
J. Yang, Z. Lei, and S. Z. Li, “Learn convolutional neural network for face anti-spoofing,” 6 2014.
Z. Ming, M. Visani, M. M. Luqman, and J. C. Burie, “A survey on anti-spoofing methods for face recognition with rgb cameras of generic
consumer devices,” arXiv, 2020.
L. Li, X. Feng, Z. Boulkenafet, Z. Xia, M. Li, and A. Hadid, “An original face anti-spoofing approach using partial convolutional neural network,” in 2016 Sixth International Conference on Image Processing Theory, Tools and Applications (IPTA), pp. 1–6, IEEE, 2016.
B. Zinelabidine, K. Jukka, L. Li, X. Feng, and A. Hadid, “Oulunpu: a mobile face presentation attack database with real-world variations,” in Proc. IEEE Int. Conf. on Identity, Security and Behavior Analysis, ISBA, pp. 1–7, 2017.
I. Chingovska, A. Anjos, and S. Marcel, “On the effectiveness of local binary patterns in face anti-spoofing,” in 2012 BIOSIG-proceedings of the international conference of biometrics special interest group (BIOSIG), pp. 1–7, IEEE, 2012.
D. Wen, H. Han, and A. K. Jain, “Face spoof detection with image distortion analysis,” IEEE Transactions on Information Forensics and
Security, vol. 10, no. 4, pp. 746–761, 2015.
X. Tan, Y. Li, J. Liu, and L. Jiang, “Face liveness detection from a single image with sparse low rank bilinear discriminative model,” in European Conference on Computer Vision, pp. 504–517, Springer, 2010.
R. R. Selvaraju, M. Cogswell, A. Das, R. Vedantam, D. Parikh, and D. Batra, “Grad-cam: Visual explanations from deep networks via
gradient-based localization,” International Journal of Computer Vision, vol. 128, p. 336–359, Oct 2019.
J. Li, Y. Wang, T. Tan, and A. K. Jain, “Live face detection based on the analysis of fourier spectra,” in Biometric technology for human identification, vol. 5404, pp. 296–303, International Society for Optics and Photonics, 2004.
A. Azarbayejani, T. Starner, B. Horowitz, and A. Pentland, “Visually controlled graphics,” IEEE Transactions on Pattern Analysis and Machine Intelligence, vol. 15, no. 6, pp. 602–605, 1993.
K. Kollreider, H. Fronthaler, and J. Bigun, “Evaluating liveness by face images and the structure tensor,” in Fourth IEEE Workshop on Automatic Identification Advanced Technologies (AutoID’05), pp. 75–80, IEEE, 2005.
G. Pan, L. Sun, Z. Wu, and S. Lao, “Eyeblink-based anti-spoofing in face recognition from a generic webcamera,” in 2007 IEEE 11th international conference on computer vision, pp. 1–8, IEEE, 2007.
K. Kollreider, H. Fronthaler, M. I. Faraj, and J. Bigun, “Real-time face detection and motion analysis with application in “liveness” assessment,” IEEE Transactions on Information Forensics and Security, vol. 2, no. 3, pp. 548–558, 2007.
B. Peixoto, C. Michelassi, and A. Rocha, “Face liveness detection under bad illumination conditions,” in 2011 18th IEEE International
Conference on Image Processing, pp. 3557–3560, IEEE, 2011.
T. Ojala, M. Pietikainen, and T. Maenpaa, “Multiresolution gray-scale and rotation invariant texture classification with local binary patterns,” IEEE Transactions on pattern analysis and machine intelligence, vol. 24, no. 7, pp. 971–987, 2002.
B. S. Manjunath and W.-Y. Ma, “Texture features for browsing and retrieval of image data,” IEEE Transactions on pattern analysis and
machine intelligence, vol. 18, no. 8, pp. 837–842, 1996.
N. Dalal and B. Triggs, “Histograms of oriented gradients for human detection,” in 2005 IEEE computer society conference on computer
vision and pattern recognition (CVPR’05), vol. 1, pp. 886–893, Ieee, 2005.
T. de Freitas Pereira, A. Anjos, J. M. De Martino, and S. Marcel, “Lbp- top based countermeasure against face spoofing attacks,” in Asian Conference on Computer Vision, pp. 121–132, Springer, 2012.
S. Bharadwaj, T. I. Dhamecha, M. Vatsa, and R. Singh, “Computationally efficient face spoofing detection with motion magnification,” in
Proceedings of the IEEE conference on computer vision and pattern recognition workshops, pp. 105–110, 2013.
A. da Silva Pinto, H. Pedrini, W. Schwartz, and A. Rocha, “Video-based face spoofing detection through visual rhythm analysis,” in 2012 25th SIBGRAPI Conference on Graphics, Patterns and Images, pp. 221–228, IEEE, 2012.
T. Wang, J. Yang, Z. Lei, S. Liao, and S. Z. Li, “Face liveness detection using 3d structure recovered from a single camera,” in 2013 international conference on biometrics (ICB), pp. 1–6, IEEE, 2013.
Y. Atoum, Y. Liu, A. Jourabloo, and X. Liu, “Face anti-spoofing using patch and depth-based cnns,” in 2017 IEEE International Joint
Conference on Biometrics (IJCB), pp. 319–328, IEEE, 2017.
K. Patel, H. Han, and A. K. Jain, “Cross-database face antispoofing with robust feature representation,” in Chinese Conference on Biometric Recognition, pp. 611–619, Springer, 2016.
A. George and S. Marcel, “Deep pixel-wise binary supervision for face presentation attack detection,” in 2019 International Conference
on Biometrics (ICB), pp. 1–8, IEEE, 2019.
Z. Wang, Z. Wang, Z. Yu, W. Deng, J. Li, T. Gao, and Z. Wang, “Domain generalization via shuffled style assembly for face anti-spoofing,” 2022.
L. Zhou, J. Luo, X. Gao, W. Li, B. Lei, and J. Leng, “Selective domain-invariant feature alignment network for face anti-spoofing,”
IEEE Transactions on Information Forensics and Security, vol. 16, pp. 5352–5365, 2021.
D. E. King, “Dlib-ml: A machine learning toolkit,” Journal of Machine Learning Research, vol. 10, pp. 1755–1758, 2009.
X. Tan, F. Song, Z. H. Zhou, and S. Chen, “Enhanced pictorial structures for precise eye localization under uncontrolled conditions,” 2009 IEEE Conference on Computer Vision and Pattern Recognition, CVPR 2009, pp. 1621–1628, 2009.
A. N. Avanaki, “Exact global histogram specification optimized for structural similarity,” Optical Review, vol. 16, no. 6, pp. 613–621, 2009.
I. Goodfellow, Y. Bengio, and A. Courville, Deep Learning. 2016.
Q. Cao, L. Shen, W. Xie, O. M. Parkhi, and A. Zisserman, “VGGFace2:
A dataset for recognising faces across pose and age,” Proceedings - 13th IEEE International Conference on Automatic Face and Gesture
Recognition, FG 2018, pp. 67–74, 2018.
K. Simonyan and A. Zisserman, “Very deep convolutional networks for large-scale image recognition,” arXiv preprint arXiv:1409.1556, 2014.
J. Deng, W. Dong, R. Socher, L.-J. Li, K. Li, and L. Fei-Fei, “Imagenet: A large-scale hierarchical image database,” in 2009 IEEE conference on computer vision and pattern recognition, pp. 248–255, Ieee, 2009.
A. Ilugbusi and A. Adetunmbi, “Development of a multi-intance fingerprint based authentication system,” pp. 1–9, 10 2017.
J. Määttä, A. Hadid, and M. Pietikäinen, “Face spoofing detection from single images using texture and local shape analysis,” IET biometrics, vol. 1, no. 1, pp. 3–10, 2012.
J. Yang, Z. Lei, S. Liao, and S. Z. Li, “Face liveness detection with component dependent descriptor,” in 2013 International Conference on Biometrics (ICB), pp. 1–6, IEEE, 2013.
S. R. Arashloo, J. Kittler, and W. Christmas, “Face spoofing detection based on multiple descriptor fusion using multiscale dynamic binarized statistical image features,” IEEE Transactions on Information Forensics and Security, vol. 10, no. 11, pp. 2396–2407, 2015.
Z. Boulkenafet, J. Komulainen, and A. Hadid, “Face anti-spoofing based on color texture analysis,” in 2015 IEEE international conference on image processing (ICIP), pp. 2636–2640, IEEE, 2015.
X. Tu, Z. Ma, J. Zhao, G. Du, M. Xie, and J. Feng, “Learning generalizable and identity-discriminative representations for face antispoofing,” ACM Transactions on Intelligent Systems and Technology (TIST), vol. 11, no. 5, pp. 1–19, 2020.
A. Jourabloo, Y. Liu, and X. Liu, “Face de-spoofing: Anti-spoofing via noise modeling,” Lecture Notes in Computer Science (including
subseries Lecture Notes in Artificial Intelligence and Lecture Notes in Bioinformatics), vol. 11217 LNCS, pp. 297–315, 2018.
Z. Boulkenafet, J. Komulainen, Z. Akhtar, A. Benlamoudi, D. Samai, S. E. Bekhouche, A. Ouafi, F. Dornaika, A. Taleb-Ahmed, L. Qin, et al., “A competition on generalized software-based face presentation attack detection in mobile scenarios,” in 2017 IEEE International Joint Conference on Biometrics (IJCB), pp. 688–696, IEEE, 2017.