An interaction-aware approach for social influence maximization
Keywords:
Social Influence Maximization, Social Network Modeling, Influencers Discovering, Viral MarketingAbstract
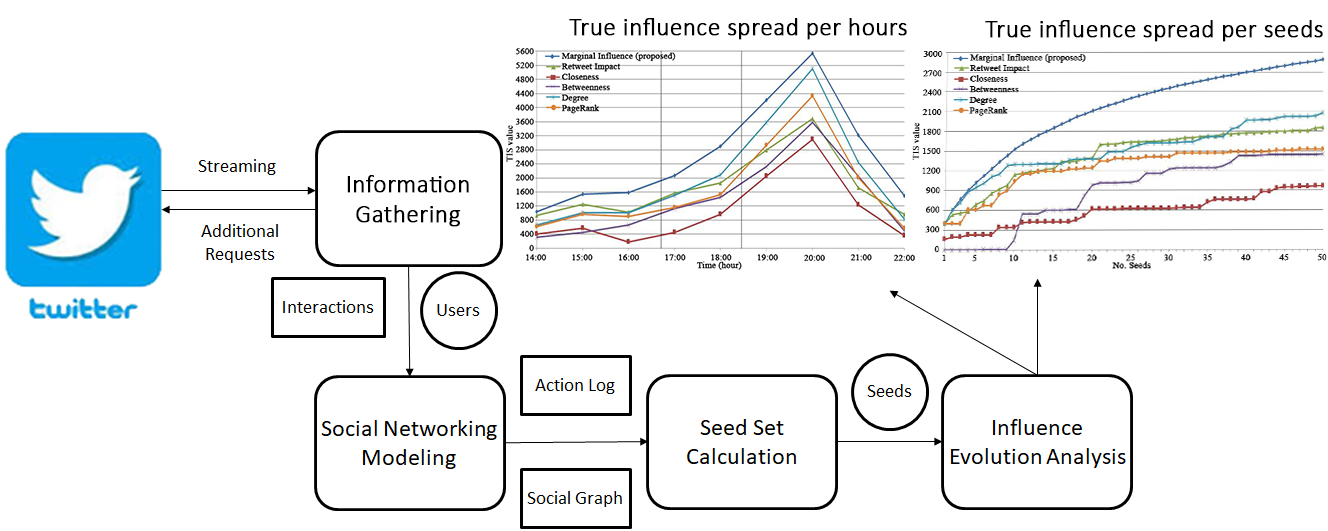
Microblogging networks are considered a great source of social influence. One of its characteristics is their high dynamism. This fact produces that influential users continuously change according with time and topic. Several social networks metrics have been defined to rank influential users. However, these metrics fail to capture the dynamism of microblogging networks. For this reason, we propose an approach based on Credit Distribution model to identify the influential users of a microblogging social network by performing an online analysis of the users’ interactions. Moreover, we present a comparison of our approach with well-known metrics used for influencers ranking. The experiments were carried out in Twitter during sport events (football matches) and new product (video games) launchings. The results showed that our approach outperforms the metric-based rankings in terms of the influence spread. This confirms the importance of being updated for identifying influential users.
Downloads
References
M. Gomez-Rodriguez, L. Song, N. Du, H. Zha, and B. Schölkopf, “Influence estimation and maximization in continuous-time diffusion networks,” ACM Trans. Inf. Syst., vol. 34, no. 2, pp. 1–33, 2016.
E. Bakshy, J. M. Hofman, W. A. Mason, and D. J. Watts, “Everyone’s an influencer: Quantifying influence on twitter,” in Proc. of the Fourth ACM Int. Conf. on Web Search and Data Mining, ser. WSDM ’11. NY, USA: ACM, 2011, pp. 65–74.
K. Devi and R. Tripathi, “An ltirs model for influence diffusion process,” in 2022 14th Int. Conf. on COMmunication Systems & NETworkS (COMSNETS). IEEE, 2022, pp. 285–289.
F. Bonchi, “Influence propagation in social networks: A data mining perspective,” in Web Intelligence and Intelligent Agent Technology (WI-IAT), 2011 IEEE/WIC/ACM Int. Conf. on, vol. 1, Aug 2011, pp. 2–2.
M. Richardson and P. Domingos, “Mining knowledge-sharing sites for viral marketing,” in Proc. of the Eighth ACM SIGKDD Int.Conf. on Knowledge Discovery and Data Mining, ser. KDD ’02. NY,USA: ACM, 2002, pp. 61–70.
V. Mahajan, E. Muller, and F. M. Bass, “New product diffusionmodels in marketing: A review and directions for research,”Journal of Marketing, vol. 54, no. 1, pp. 1–26, 1990.
D. Kempe, J. Kleinberg, and E. Tardos, “Maximizing the spread of influence through a social network,” in Proc. of the Ninth ACM SIGKDD Int. Conf. on Knowledge Discovery and Data Mining, ser. KDD ’03. NY, USA: ACM, 2003, pp. 137–146.
C. M. Bishop, Pattern Recognition and Machine Learning (Information Science and Statistics). Berlin, Heidelberg: Springer-Verlag, 2006.
M. R. Everett, “Diffusion of innovations,” Simon and Schuster, vol. 12, 2010.
A. Goyal, F. Bonchi, and L. V. Lakshmanan, “Learning influence probabilities in social networks,” in Proc. of the Third ACM Int. Conf. on Web Search and Data Mining, ser. WSDM ’10. NY, USA: ACM, 2010, pp. 241–250.
M. Gomez-Rodriguez, J. Leskovec, and A. Krause, “Inferring networks of diffusion and influence,” ACM Trans. Knowl. Discov. Data, vol. 5, no. 4, feb 2012.
K. Saito, M. Kimura, K. Ohara, and H. Motoda, “Selecting information diffusion models over social networks for behavioural analysis,” in Proc. of the 2010 European Conf. on Machine Learning and Knowledge Discovery in Databases: Part III, ser. ECML PKDD’10. Berlin, Heidelberg: Springer-Verlag, 2010, pp. 180–195.
A. Goyal, F. Bonchi, and L. V. S. Lakshmanan, “A data-based approach to social influence maximization,” PVLDB, vol. 5, no. 1, pp. 73–84, 2011.
L. Rashotte, “Social influence,” The Blackwell encyclopedia of sociology, 2007.
C. Long and R. C.-W. Wong, “Viral marketing for dedicated customers,” Inf. Syst., vol. 46, pp. 1–23, dec 2014.
J. Goldenberg, B. Libai, and E. Muller, “Talk of the network: A complex systems look at the underlying process of word-ofmouth,” Marketing Letters, vol. 12, pp. 211–223, 2001.
B. Liu, G. Cong, Y. Zeng, D. Xu, and Y. M. Chee, “Influence spreading path and its application to the time constrained social influence maximization problem and beyond,” IEEE Transactions on Knowledge and Data Engineering, vol. 26, no. 8, pp. 1904–1917, 2014.
B. Doerr, M. Fouz, and T. Friedrich, “Why rumors spread so quickly in social networks,” Commun. ACM, vol. 55, no. 6, pp. 70–75, jun 2012.
P. Beaumont, “The truth about twitter, facebook and the uprisings in the arab world,” in The Guardian, vol. 25, 2011.
W. Chen, W. Lu, and N. Zhang, “Time-critical influence maximization in social networks with time-delayed diffusion process,” in Proc. of the Twenty-Sixth AAAI Conf. on Artificial Intelligence, ser. AAAI’12. AAAI Press, 2012, pp. 592–598.
T. Shi, J. Wan, S. Cheng, Z. Cai, Y. Li, and J. Li, “Time-bounded positive influence in social networks,” in 2015 Int. Conf. on Identification, Information, and Knowledge in the Internet of Things (IIKI), 2015, pp. 134–139.
D. Golovin and A. Krause, “Adaptive submodularity: A new approach to active learning and stochastic optimization,” CoRR, vol. abs/1003.3967, 2010.
Y. Chen and A. Krause, “Near-optimal batch mode active learning and adaptive submodular optimization,” in Proc. of the 30th Int. Conf. on Machine Learning, ICML 2013, Atlanta, GA, USA, 16-21 June 2013, ser. JMLR Workshop and Conf. Proc., vol. 28. JMLR.org, 2013, pp. 160–168.
S. Vaswani and L. V. S. Lakshmanan, “Adaptive influence maximization in social networks: Why commit when you can adapt?”ArXiv, vol. abs/1604.08171, 2016.
F. Riquelme and P. G. Cantergiani, “Measuring user influence on twitter: A survey,” Inf. Process. Manag., vol. 52, pp. 949–975, 2016.
D. M. Romero, B. Meeder, and J. Kleinberg, “Differences in the mechanics of information diffusion across topics: Idioms, political hashtags, and complex contagion on twitter,” in Proc. of the 20th Int. Conf. on World Wide Web, ser. WWW ’11. NY, USA: ACM, 2011, pp. 695–704.
L. C. Freeman, “Centrality in social networks conceptual clarification,” Social Networks, p. 215, 1978.
X. Jin and Y. Wang, “Research on social network structure and public opinions dissemination of micro-blog based on complex
network analysis,” J. Networks, vol. 8, no. 7, pp. 1543–1550, 2013.
L. Page, S. Brin, R. Motwani, and T. Winograd, “The pagerank citation ranking: Bringing order to the web.” Stanford InfoLab,
Technical Report 1999-66, November 1999, previous number = SIDL-WP-1999-0120.
J. Zhang, R. Zhang, J. Sun, Y. Zhang, and C. Zhang, “Truetop: A sybil-resilient system for user influence measurement on twitter,” IEEE/ACM Transactions on Networking, vol. 24, pp. 2834–2846, 2016.
A. Pal and S. Counts, “Identifying topical authorities in microblogs,” in Proc. of the Fourth ACM Int. Conf. on Web Search and Data Mining, ser. WSDM ’11. NY, USA: ACM, 2011, pp. 45–54.
Y. Li, J. Fan, Y. Wang, and K.-L. Tan, “Influence maximization on social graphs: A survey,” IEEE Transactions on Knowledge and Data Engineering, vol. 30, no. 10, pp. 1852–1872, 2018.
K. Jung, W. Heo, and W. Chen, “Irie: Scalable and robust influence maximization in social networks,” 2012 IEEE 12th Int. Conf. on Data Mining, pp. 918–923, 2012.
W. Liang, C. Shen, X. Li, R. Nishide, I. Piumarta, and H. Takada, “Influence maximization in signed social networks with opinion formation,” IEEE Access, vol. 7, pp. 68 837–68 852, 2019.
G. Xie, Y. Chen, H. Zhang, and Y. Liu, “Mbic: A novel influence propagation model for membership-based influence maximization in social networks,” IEEE Access, vol. 7, pp. 75 696–75 707, 2019.
M. Lahiri and M. Cebrian, “The genetic algorithm as a general diffusion model for social networks,” in Proc. of the Twenty-Fourth AAAI Conf. on Artificial Intelligence, ser. AAAI’10. AAAI Press, 2010, pp. 494–499.
J. Leskovec, A. Krause, C. Guestrin, C. Faloutsos, J. VanBriesen, and N. Glance, “Cost-effective outbreak detection in networks,” in Proc. of the 13th ACM SIGKDD Int. Conf. on Knowledge Discovery and Data Mining, ser. KDD ’07. NY, USA: ACM, 2007, pp. 420–429.