MELTWEB: A Transient Execution Attack to Capture Data in Fill Line Buffer.
Keywords:
Meltweb, Meltdown, Transient Execution AttacksAbstract
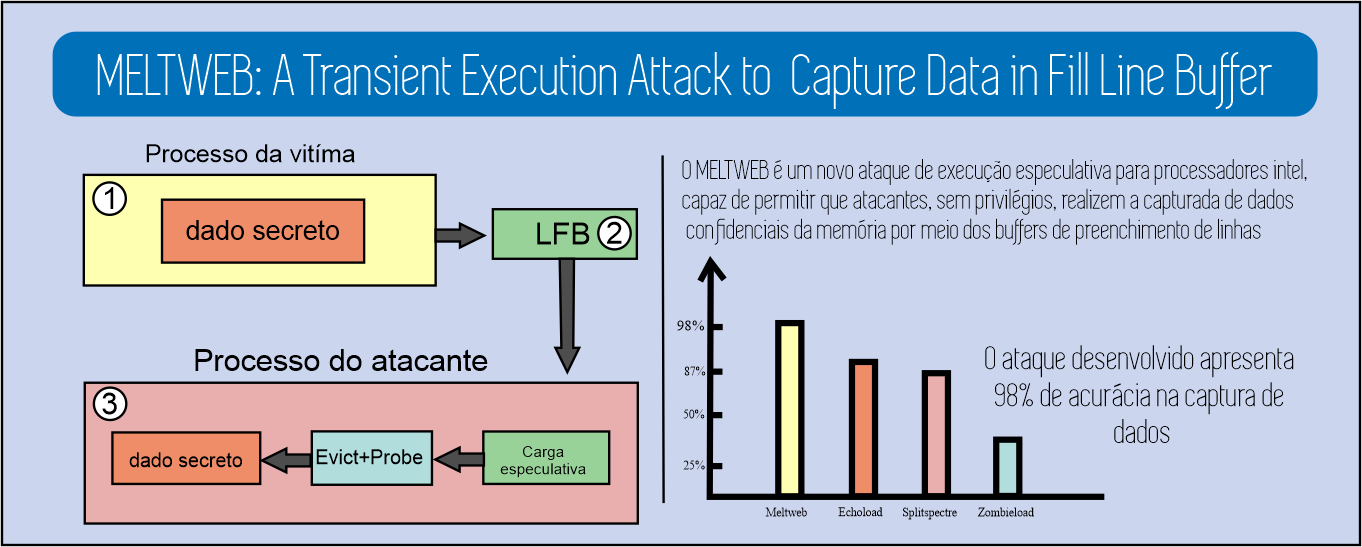
The out-of-order execution mechanism is widely used in modern processors. However, meltdown attacks exploit this mechanism to allow malicious instructions to capture sensitive data from kernel domains. This work aims to present a new meltdown attack, called Meltweb. It is a new approach in the category of privileged speculative execution attacks to leak arbitrary data into address spaces and privilege limits. Meltweb can be implemented from linear execution without the need for page faults, eliminating the need for an exception suppression mechanism, thus allowing the attack to be executed throughout the system of arbitrary code without privileges as in search engines interpretation of Javascript. To exemplify the performance of the attack, two proof-of-concept variants were developed that demonstrate the ability to perform the attack natively, as well as remotely using Javascript. The attack developed showed satisfactory results in its two variants, with 98\% accuracy in capturing confidential data in the native variant. For the remote variant, the attack proved to be capable of capturing navigation data as a URL recovery with an error rate of 2.3%.
Downloads
References
P. Kocher, J. Horn, A. Fogh, D. Genkin, D. Gruss, W. Haas, M. Ham-burg, M. Lipp, S. Mangard, T. Prescher,et al., “Spectre attacks: Exploi-ting speculative execution.,”In Proceedings on Security and Privacy Symposium, pp. 1–19, 06 2019.
M. Lipp, M. Schwarz, D. Gruss, T. Prescher, W. Haas, A. Fogh, J. Horn,S. Mangard, P. Kocher, D. Genkin,et al., “Meltdown: Reading kernel memory from user space,”In: Proceedings of the Usenix Security Symposium, pp. 973–990, 06 2018.
V. Kiriansky and C. Waldspurger, “Speculative buffer overflows: Attacks and defenses,”In: Proceedings preprint arXiv, 2018.
G. Maisuradze and C. Rossow, “ret2spec: Speculative execution using return stack buffers,” in Proceedings of the Conference on Computer and Communications Security, pp. 2109–2122, 2018.
E. M. Koruyeh, K. N. Khasawneh, C. Song, and N. Abu-Ghazaleh,“Spectre returns! speculation attacks using the return stack buffer,” in Workshop on Offensive Technologies, (New York), IEEE, 2018.
J. Wampler, I. Martiny, and E. Wustrow, “Exspectre: Hiding malware in speculative execution.,” in Proceedings of the Network and Distributed System Security Symposium, 2019.
C. Canella, D. Genkin, L. Giner, D. Gruss, M. Lipp, M. Minkin,D. Moghimi, F. Piessens, M. Schwarz, B. Sunar,et al., “Fallout: Leaking data on meltdown-resistant cpus,” in Proceedings of the Conference on Computer and Communications Security, (New York, NY, USA),p. 769–784, Association for Computing Machinery, 2019.
J. Stecklina and T. Prescher, “Lazyfp: Leaking fpu register state using microarchitectural side-channels,”arXiv preprint, 2018.
M. Schwarz, M. Lipp, D. Moghimi, J. Van Bulck, J. Stecklina, T. Pres-cher, and D. Gruss, “Zombieload: Cross-privilege-boundary data sampling.,”In Proceedings Conference on Computer and Communications Security, pp. 1–19, 06 2019.
J. Van Bulck, D. Moghimi, M. Schwarz, M. Lippi, M. Minkin, D. Gen-kin, Y. Yarom, B. Sunar, D. Gruss, and F. Piessens, “Foreshadow: Extracting the keys to the intel sgx kingdom with transient out-of-order execution,” in Security Symposium Security, (New York, NY, USA),pp. 991–1008, Association for Computing Machinery, 2018.
J. Van Bulck, D. Moghimi, M. Schwarz, M. Lippi, M. Minkin,D. Genkin, Y. Yarom, B. Sunar, D. Gruss, and F. Piessens, “LVI: Hijacking Transient Execution through Microarchitectural Load ValueInjection,” in Symposium on Security and Privacy, (New York, NY,USA), Association for Computing Machinery, 2020.
V. Kiriansky, I. Lebedev, S. Amarasinghe, S. Devadas, and J. Emer,“Dawg: A defense against cache timing attacks in speculative execution processors,” in Proceedings of the International Symposium on Micro-architecture, pp. 974–987, IEEE, 2018.
M. Yan, J. Choi, D. Skarlatos, A. Morrison, C. Fletcher, and J. Tor-rellas, “Invisispec: Making speculative execution invisible in the cache hierarchy,” in Proceedings of the International Symposium on Microarchitecture, pp. 428–441, IEEE, 2018.
K. N. Khasawneh, E. M. Koruyeh, C. Song, D. Evtyushkin, D. Ponomarev, and N. Abu-Ghazaleh, “Safespec: Banishing the spectre of a meltdown with leakage-free speculation,” in Proceedings of the Design Automation Conference, pp. 1–6, IEEE, 2019.
A. Bilal, “Real time detection of spectre and meltdown attacks using machine learning.,”Proceedings of the Conference on Security Symposium, 2020.
C. Canella, J. Van Bulck, M. Schwarz, M. Lipp, B. Von Berg, P. Ortner,F. Piessens, D. Evtyushkin, and D. Gruss, “A systematic evaluation of transient execution attacks and defenses.” in Proceedings of theConference on Computer and Communications Security, (New York,NY, USA), pp. 943–959, USENIX, 2020.
C. Canella, M. Schwarz, M. Haubenwallner, M. Schwarzl, and D. Gruss,“Kaslr: Break it, fix it, repeat,”Proceedings of the Asia Conference on Computer and Communications Security, 2020.
D. Gruss, R. Spreitzer, and S. Mangard, “Cache template attacks: Automating attacks on inclusive last-level caches” p. 897–912, 2015.
M. Lipp, D. Gruss, R. Spreitzer, C. Maurice, and S. Mangard, “Armaged-don: Cache attacks on mobile devices,” in Proceedings of the USENIXConference on Security Symposium, 2016.
D. Gruss, C. Maurice, K. Wagner, and S. Mangard, “Flush+flush: A fast and stealthy cache attack” in Proceedings of the International Conference on Detection of Intrusions and Malware, and Vulnerability Assessment, (Berlin, Heidelberg), p. 279–299, Springer-Verlag, 2016.
R. Hund, C. Willems, and T. Holz, “Practical timing side channel attacks against kernel space aslr,” in Proceedings Symposium on Security and Privacy, (New York, NY, USA), pp. 191–205, IEEE, 2013.
P. Frigo, C. Giuffrida, H. Bos, and K. Razavi, “Grand pwning unit: Accelerating microarchitectural attacks with the gpu,” in 2018 IEEE Symposium on Security and Privacy (SP), pp. 195–210, IEEE, 2018.
A. Mambretti, M. Neugschwandtner, A. Sorniotti, E. Kirda, W. Robert-son, and A. Kurmus, “Let’s not speculate: Discovering and analyzing speculative execution attacks,”IBM Research, 2018.
H. Mei, G. Huang, and T. Xie, “Internetware: A software paradigm for internet computing,”Computer and systems, vol. 45, pp. 26–31, 2012.