A Review of Privacy-Preserving Aggregation Schemes for Smart Grid
Keywords:
Smart Grids, Data privacy, Security, Information security, Cryptography , Meter reading, Power DistributionAbstract
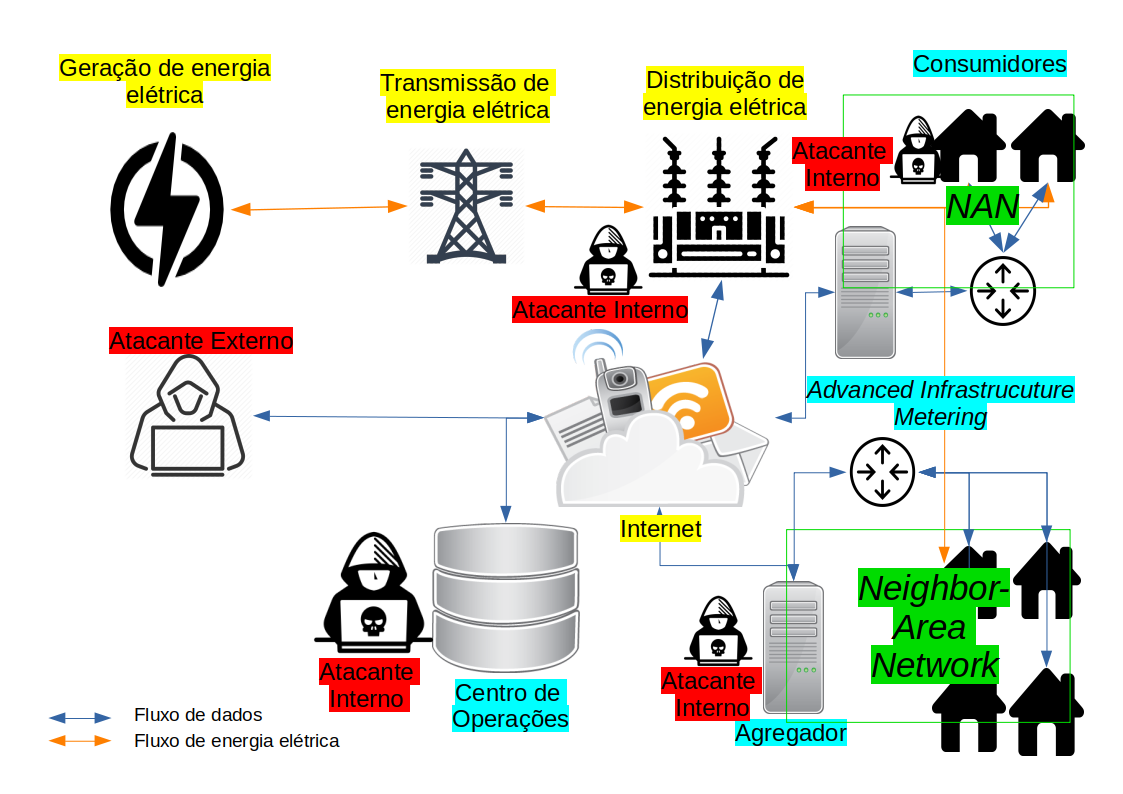
Smart Grid aims to make the use of electricity reliable, sustainable, scalable, fault-tolerant, and efficient. For this purpose, it uses information and communication technologies. However, there are issues related to information security threats. For example, an adversary monitoring data metering from consumers could trace their habits. Traditional encryption techniques resolve this question against external attackers. However, the operation center still could trace the consumer’s habits. Thus, to preserve consumer’s privacy, even against internal threats, the data must be aggregated by groups of consumers, representing a geographic area. A usual way to make it possible is through the use of homomorphic cryptography, since it allows making arithmetic operation over encrypted data. Thus, this article reviews the literature on privacy-preserving data aggregation schemes against internal and external attackers. It also presents the information security requirements for Advanced Metering Infrastructure (AMI) and its operation.
Downloads
References
Z. Baloch, F. K. Shaikh, and M. A. Unar, “A context-aware data fusion approach for health-iot,” International Journal of Information Technology, vol. 10, no. 3, pp. 241–245, 2018.
I. Mat, M. R. M. Kassim, A. N. Harun, and I. M. Yusoff, “Iot in precision agriculture applications using wireless moisture sensor network,” in 2016 IEEE Conference on Open Systems (ICOS). IEEE, 2016, pp. 24–29.
S. Anwar and D. Kishore, “Iot based smart home security system with alert and door access control using smart phone,” International Journal of Engineering Research & Technology (IJERT), vol. 5, no. 12, pp. 504–509, 2016.
H. T. Haider, O. H. See, and W. Elmenreich, “A review of residential demand response of smart grid,” Renewable and Sustainable Energy Reviews, vol. 59, pp. 166–178, 2016.
M. Hossain, N. Madlool, N. Rahim, J. Selvaraj, A. Pandey, and A. F. Khan, “Role of smart grid in renewable energy: An overview,” Renewable and Sustainable Energy Reviews, vol. 60, pp. 1168–1184, 2016.
W. Fernandez and A. Rodriguez, “Analysis of the regulatory requirements for the smart grid in chile,” IEEE Latin America Transactions, vol. 15, no. 1, pp. 13–20, 2017.
Y. Lopes, N. C. Fernandes, and K. Obraczka, “Smart grid communication: Requirements and scada protocols analysis,” in 2018 Simposio Brasileiro de Sistemas Eletricos (SBSE). IEEE, 2018, pp. 1–6.
Mendel, Jacob and others, “Smart grid cyber security challenges: Overview and classification,” e-mentor, vol. 68, no. 1, pp. 55–66, 2017.
S.-K. Kim and J.-H. Huh, “A study on the improvement of smart grid security performance and blockchain smart grid perspective,” Energies, vol. 11, no. 8, p. 1973, 2018.
R. Zafar, A. Mahmood, S. Razzaq, W. Ali, U. Naeem, and K. Shehzad, “Prosumer based energy management and sharing in smart grid,” Renewable and Sustainable Energy Reviews, vol. 82, pp. 1675–1684, 2018.
S. Tan, D. De, W.-Z. Song, J. Yang, and S. K. Das, “Survey of security advances in smart grid: A data driven approach,” IEEE Communications Surveys & Tutorials, vol. 19, no. 1, pp. 397–422, 2017.
W. Wang and Z. Lu, “Cyber security in the smart grid: Survey and challenges,” Computer networks, vol. 57, no. 5, pp. 1344–1371, 2013.
H. He and J. Yan, “Cyber-physical attacks and defences in the smart grid: a survey,” IET Cyber-Physical Systems: Theory & Applications, vol. 1, no. 1, pp. 13–27, 2016.
Z. El Mrabet, N. Kaabouch, H. El Ghazi, and H. El Ghazi, “Cybersecurity in smart grid: Survey and challenges,” Computers & Electrical Engineering, vol. 67, pp. 469–482, 2018.
Z. Fan, P. Kulkarni, S. Gormus, C. Efthymiou, G. Kalogridis, M. Sooriyabandara, Z. Zhu, S. Lambotharan, and W. H. Chin, “Smart grid communications: Overview of research challenges, solutions, and standardization activities,” IEEE Communications Surveys & Tutorials, vol. 15, no. 1, pp. 21–38, 2012.
N. Good, K. A. Ellis, and P. Mancarella, “Review and classification of barriers and enablers of demand response in the smart grid,” Renewable and Sustainable Energy Reviews, vol. 72, pp. 57–72, 2017.
R. Bayindir, I. Colak, G. Fulli, and K. Demirtas, “Smart grid technologies and applications,” Renewable and Sustainable Energy Reviews, vol. 66, pp. 499–516, 2016.
M. Emmanuel and R. Rayudu, “Communication technologies for smart grid applications: A survey,” Journal of Network and Computer Applications, vol. 74, pp. 133–148, 2016.
Y. Kabalci, “A survey on smart metering and smart grid communication,” Renewable and Sustainable Energy Reviews, vol. 57, pp. 302–318, 2016.
S. Sultan, “Privacy-preserving metering in smart grid for billing, operational metering, and incentive-based schemes: A survey,” Computers & Security, vol. 84, pp. 148–165, 2019.
M. A. Ferrag, L. A. Maglaras, H. Janicke, and J. Jiang, “A survey on privacy-preserving schemes for smart grid communications,” arXiv preprint arXiv:1611.07722, 2016.
M. Rogozinski and R. F. Calili, “Smart grid security applied to the brazilian scenario: A visual approach,” IEEE Latin America Transactions, vol. 100, no. 1e, 2020.
A. K. Sangaiah, D. V. Medhane, G.-B. Bian, A. Ghoneim, M. Alrashoud, and M. S. Hossain, “Energy-aware green adversary model for cyberphysical security in industrial system,” IEEE Transactions on Industrial Informatics, vol. 16, no. 5, pp. 3322–3329, 2019.
M. L. Tuballa and M. L. Abundo, “A review of the development of smart grid technologies,” Renewable and Sustainable Energy Reviews, vol. 59, pp. 710–725, 2016.
R. Ullah, Y. Faheem, and B. Kim, “Energy and congestion-aware routing metric for smart grid ami networks in smart city,” IEEE Access, vol. 5, pp. 13 799–13 810, 2017.
M. H. Cintuglu, O. A. Mohammed, K. Akkaya, and A. S. Uluagac, “A survey on smart grid cyber-physical system testbeds,” IEEE Communications Surveys & Tutorials, vol. 19, no. 1, pp. 446–464, 2016.
R. Deng, Z. Yang, M.-Y. Chow, and J. Chen, “A survey on demand response in smart grids: Mathematical models and approaches,” IEEE Transactions on Industrial Informatics, vol. 11, no. 3, pp. 570–582, 2015.
S. Nimbargi, S. Mhaisne, S. Nangare, and M. Sinha, “Review on ami technology for smart meter,” in 2016 IEEE International Conference on Advances in Electronics, Communication and Computer Technology (ICAECCT). IEEE, 2016, pp. 21–27.
Z. Erkin, J. R. Troncoso-Pastoriza, R. L. Lagendijk, and F. P´erez-Gonz´alez, “Privacy-preserving data aggregation in smart metering systems: An overview,” IEEE Signal Processing Magazine, vol. 30, no. 2, pp. 75–86, 2013.
H. H. Safa, D. M. Souran, M. Ghasempour, and A. Khazaee, “Cyber security of smart grid and scada systems, threats and risks,” in CIRED Workshop 2016, 2016, pp. 1–4.
M. Benmalek, Y. Challal, A. Derhab, and A. Bouabdallah, “Versami: Versatile and scalable key management for smart grid ami systems,” Computer Networks, vol. 132, pp. 161–179, 2018.
K. G. Di Santo, E. Kanashiro, S. G. Di Santo, and M. A. Saidel, “A review on smart grids and experiences in brazil,” Renewable and Sustainable Energy Reviews, vol. 52, pp. 1072–1082, 2015.
A. Ghosal and M. Conti, “Key management systems for smart grid advanced metering infrastructure: A survey,” IEEE Communications Surveys Tutorials, vol. 21, no. 3, pp. 2831–2848, 2019.
M. Shrestha, C. Johansen, J. Noll, and D. Roverso, “A methodology for security classification applied to smart grid infrastructures,” International Journal of Critical Infrastructure Protection, vol. 28, p. 100342, 2020.
V. Odelu, A. K. Das, M. Wazid, and M. Conti, “Provably secure authenticated key agreement scheme for smart grid,” IEEE Transactions on Smart Grid, vol. 9, no. 3, pp. 1900–1910, 2016.
R. R. Mohassel, A. Fung, F. Mohammadi, and K. Raahemifar, “A survey on advanced metering infrastructure,” International Journal of Electrical Power & Energy Systems, vol. 63, pp. 473–484, 2014.
N. Saputro and K. Akkaya, “Investigation of smart meter data reporting strategies for optimized performance in smart grid ami networks,” IEEE Internet of Things Journal, vol. 4, no. 4, pp. 894–904, 2017.
Y. Yoldas¸, A. O¨ nen, S. Muyeen, A. V. Vasilakos, and I˙. Alan, “Enhancing smart grid with microgrids: Challenges and opportunities,” Renewable and Sustainable Energy Reviews, vol. 72, pp. 205–214, 2017.
E. U. Haq, H. Xu, L. Pan, and M. I. Khattak, “Smart grid security: threats and solutions,” in 2017 13th International Conference on Semantics, Knowledge and Grids (SKG). IEEE, 2017, pp. 188–193.
B. Gupta and T. Akhtar, “A survey on smart power grid: frameworks, tools, security issues, and solutions,” Annals of Telecommunications, vol. 72, no. 9-10, pp. 517–549, 2017.
E. Irmak and ˙I. Erkek, “An overview of cyber-attack vectors on scada systems,” in 2018 6th International Symposium on Digital Forensic and Security (ISDFS). IEEE, 2018, pp. 1–5.
W. Alves, D. Martins, U. Bezerra, and A. Klautau, “A hybrid approach for big data outlier detection from electric power scada system,” IEEE Latin America Transactions, vol. 15, no. 1, pp. 57–64, 2017.
V. K. Singh, H. Ebrahem, and M. Govindarasu, “Security evaluation of two intrusion detection systems in smart grid scada environment,” in 2018 North American Power Symposium (NAPS). IEEE, 2018, pp. 1–6.
K. R. Khan, A. Rahman, A. Nadeem, M. S. Siddiqui, and R. A. Khan, “Remote monitoring and control of microgrid using smart sensor network and internet of thing,” in 2018 1st International Conference on Computer Applications Information Security (ICCAIS), 2018, pp. 1–4.
M. Marian, A. Cusman, D. Popescu, and D. Ionic˘a, “A dnp3-based scada architecture supporting electronic signatures,” in 2019 20th International Carpathian Control Conference (ICCC), 2019, pp. 1–6.
F. Espinoza, M. Mar, E. Ramirez, and J. Noel, “Control of real power in a synchronous machine using a scada system in a smart grid,” in 2016 IEEE ANDESCON, 2016, pp. 1–4.
I. Colak, S. Sagiroglu, G. Fulli, M. Yesilbudak, and C.-F. Covrig, “A survey on the critical issues in smart grid technologies,” Renewable and Sustainable Energy Reviews, vol. 54, pp. 396–405, 2016.
Y. Zhang, L. Wang, Y. Xiang, and C.-W. Ten, “Power system reliability evaluation with scada cybersecurity considerations,” IEEE Transactions on Smart Grid, vol. 6, no. 4, pp. 1707–1721, 2015.
A. Anwar, A. Mahmood, and M. Pickering, “Estimation of smart grid topology using scada measurements,” in 2016 IEEE International Conference on Smart Grid Communications (SmartGridComm), 2016, pp. 539–544.
A. O. Otuoze, M. W. Mustafa, and R. M. Larik, “Smart grids security challenges: Classification by sources of threats,” Journal of Electrical Systems and Information Technology, vol. 5, no. 3, pp. 468–483, 2018.
P. Kumar, Y. Lin, G. Bai, A. Paverd, J. S. Dong, and A. Martin, “Smart grid metering networks: A survey on security, privacy and open research issues,” IEEE Communications Surveys & Tutorials, vol. 21, no. 3, pp. 2886–2927, 2019.
S. Garg, K. Kaur, G. Kaddoum, J. J. P. C. Rodrigues, and M. Guizani, “Secure and lightweight authentication scheme for smart metering infrastructure in smart grid,” IEEE Transactions on Industrial Informatics, vol. 16, no. 5, pp. 3548–3557, 2020.
C. Ruland and J. Sassmannshausen, “System-wide traceability of commands and data exchange in smart grids,” in 2019 International Conference on Smart Energy Systems and Technologies (SEST). IEEE, 2019, pp. 1–6.
K. Mahmood, S. A. Chaudhry, H. Naqvi, S. Kumari, X. Li, and A. K. Sangaiah, “An elliptic curve cryptography based lightweight authentication scheme for smart grid communication,” Future Generation Computer Systems, vol. 81, pp. 557–565, 2018.
T. Zhang, T. Zhang, X. Ji, and W. Xu, “Cuckoo-rpl: Cuckoo filter based rpl for defending ami network from blackhole attacks,” in 2019 Chinese Control Conference (CCC), 2019, pp. 8920–8925.
R. C. Diovu and J. T. Agee, “A cloud-based openflow firewall for mitigation against ddos attacks in smart grid ami networks,” in 2017 IEEE PES PowerAfrica, 2017, pp. 28–33.
R. Mahmud, R. Vallakati, A. Mukherjee, P. Ranganathan, and A. Nejadpak, “A survey on smart grid metering infrastructures: Threats and solutions,” in 2015 IEEE International Conference on Electro/Information Technology (EIT). IEEE, 2015, pp. 386–391.
Ghosal, Amrita and Conti, Mauro, “Key management systems for smart grid advanced metering infrastructure: A survey,” IEEE Communications Surveys & Tutorials, vol. 21, no. 3, pp. 2831–2848, 2019.
R. K. Pandey and M. Misra, “Cyber security threats—smart grid infrastructure,” in 2016 National Power Systems Conference (NPSC). IEEE, 2016, pp. 1–6.
J. Giraldo, A. C´ardenas, and N. Quijano, “Integrity attacks on realtime pricing in smart grids: Impact and countermeasures,” IEEE Transactions on Smart Grid, vol. 8, no. 5, pp. 2249–2257, 2017.
S. Tan, W. Song, M. Stewart, J. Yang, and L. Tong, “Online data integrity attacks against real-time electrical market in smart grid,” IEEE Transactions on Smart Grid, vol. 9, no. 1, pp. 313–322, 2018.
Rizzetti, Tiago Antonio and others, “Novos m´etodos para prover seguranc¸a `a comunicac¸ ˜ao no ˆambito de redes el´etricas inteligentes,” Ph.D. dissertation, Universidade Federal de Santa Maria, 2018.
M. Z. Gunduz and R. Das, “Analysis of cyber-attacks on smart grid applications,” in 2018 International Conference on Artificial Intelligence and Data Processing (IDAP), 2018, pp. 1–5.
A. Sanjab, W. Saad, I. Guvenc, A. Sarwat, and S. Biswas, “Smart grid security: Threats, challenges, and solutions,” arXiv preprint ar-Xiv:1606.06992, 2016.
U. Ozgur, S. Tonyali, K. Akkaya, and F. Senel, “Comparative evaluation of smart grid ami networks: Performance under privacy,” in 2016 IEEE Symposium on Computers and Communication (ISCC), 2016, pp. 1134–1136.
A. Acar, H. Aksu, A. S. Uluagac, and M. Conti, “A survey on homomorphic encryption schemes: Theory and implementation,” ACM Computing Surveys (CSUR), vol. 51, no. 4, p. 79, 2018.
J. H. Cheon, A. Kim, M. Kim, and Y. Song, “Homomorphic encryption for arithmetic of approximate numbers,” in International Conference on the Theory and Application of Cryptology and Information Security. Springer, 2017, pp. 409–437.
Chase, Melissa and Chen, Hao and Ding, Jintai and Goldwasser, Shafi and Gorbunov, Sergey and Hoffstein, Jeffrey and Lauter, Kristin and Lokam, Satya and Moody, Dustin and Morrison, Travis and others, “Security of homomorphic encryption,” HomomorphicEncryption. org, Redmond WA, Tech. Rep, 2017.
P. V. Parmar, S. B. Padhar, S. N. Patel, N. I. Bhatt, and R. H. Jhaveri, “Survey of various homomorphic encryption algorithms and schemes,” International Journal of Computer Applications, vol. 91, no. 8, 2014.
C. Gentry and D. Boneh, A fully homomorphic encryption scheme. Stanford University Stanford, 2009, vol. 20, no. 09.
M. Alloghani, M. M. Alani, D. Al-Jumeily, T. Baker, J. Mustafina, A. Hussain, and A. J. Aljaaf, “A systematic review on the status and progress of homomorphic encryption technologies,” Journal of Information Security and Applications, vol. 48, p. 102362, 2019.
P. Paillier, “Public-key cryptosystems based on composite degree residuosity classes,” in International Conference on the Theory and Applications of Cryptographic Techniques. Springer, 1999, pp. 223–238.
G. Blakley and I. Borosh, “Rivest-shamir-adleman public key cryptosystems do not always conceal messages,” Computers & Mathematics with Applications, vol. 5, no. 3, pp. 169–178, 1979.
K. Wang, M. Du, S. Maharjan, and Y. Sun, “Strategic honeypot game model for distributed denial of service attacks in the smart grid,” IEEE Transactions on Smart Grid, vol. 8, no. 5, pp. 2474–2482, 2017.
S. Finster and I. Baumgart, “Privacy-aware smart metering: A survey,” IEEE Communications Surveys & Tutorials, vol. 17, no. 2, pp. 1088–1101, 2015.
W. Tong, L. Lu, Z. Li, J. Lin, and X. Jin, “A survey on intrusion detection system for advanced metering infrastructure,” in 2016 Sixth International Conference on Instrumentation Measurement, Computer, Communication and Control (IMCCC), 2016, pp. 33–37.
B. Tang, J. Yan, S. Kay, and H. He, “Detection of false data injection attacks in smart grid under colored gaussian noise,” in 2016 IEEE Conference on Communications and Network Security (CNS). IEEE, 2016, pp. 172–179.
C.-I. Fan, S.-Y. Huang, and Y.-L. Lai, “Privacy-enhanced data aggregation scheme against internal attackers in smart grid,” IEEE Transactions on Industrial informatics, vol. 10, no. 1, pp. 666–675, 2013.
N. V. Abhishek, T. J. Lim, B. Sikdar, and A. Tandon, “An intrusion detection system for detecting compromised gateways in clustered iot networks,” in 2018 IEEE International Workshop Technical Committee on Communications Quality and Reliability (CQR). IEEE, 2018, pp. 1–6.
S. Desai, R. Alhadad, N. Chilamkurti, and A. Mahmood, “A survey of privacy preserving schemes in ioe enabled smart grid advanced metering infrastructure,” Cluster Computing, vol. 22, no. 1, pp. 43–69, 2019.
Y. Sun, L. Lampe, and V. W. S. Wong, “Ev-assisted battery load hiding: A markov decision process approach,” in 2016 IEEE International Conference on Smart Grid Communications (SmartGridComm), 2016, pp. 160–166.
M. Nabeel, S. Kerr, X. Ding, and E. Bertino, “Authentication and key management for advanced metering infrastructures utilizing physically unclonable functions,” in 2012 IEEE Third International Conference on Smart Grid Communications (SmartGridComm). IEEE, 2012, pp. 324–329.
R. Lu, X. Liang, X. Li, X. Lin, and X. Shen, “Eppa: An efficient and privacy-preserving aggregation scheme for secure smart grid communications,” IEEE Transactions on Parallel and Distributed Systems, vol. 23, no. 9, pp. 1621–1631, 2012.
M.-S. Lacharit´e, “Security of bls and bgls signatures in a multi-user setting,” Cryptography and Communications, vol. 10, no. 1, pp. 41–58, 2018.
D. Boneh, B. Lynn, and H. Shacham, “Short signatures from the weil pairing,” in International Conference on the Theory and Application of Cryptology and Information Security. Springer, 2001, pp. 514–532.
S. Tonyali, K. Akkaya, N. Saputro, A. S. Uluagac, and M. Nojoumian, “Privacy-preserving protocols for secure and reliable data aggregation in iot-enabled smart metering systems,” Future Generation Computer Systems, vol. 78, pp. 547–557, 2018.
H. Li, X. Lin, H. Yang, X. Liang, R. Lu, and X. Shen, “Eppdr: An efficient privacy-preserving demand response scheme with adaptive key evolution in smart grid,” IEEE Transactions on Parallel and Distributed Systems, vol. 25, no. 8, pp. 2053–2064, 2013.
A. Sahai and B. Waters, “Fuzzy identity-based encryption,” in Annual International Conference on the Theory and Applications of Cryptographic Techniques. Springer, 2005, pp. 457–473.
R. Lu, K. Alharbi, X. Lin, and C. Huang, “A novel privacy-preserving set aggregation scheme for smart grid communications,” in 2015 IEEE global communications conference (GLOBECOM). IEEE, 2015, pp. 1–6.
J. Ni, K. Alharbi, X. Lin, and X. Shen, “Security-enhanced data aggregation against malicious gateways in smart grid,” in 2015 IEEE Global Communications Conference (GLOBECOM). IEEE, 2015, pp. 1–6.
X. Dong, J. Zhou, K. Alharbi, X. Lin, and Z. Cao, “An elgamal-based efficient and privacy-preserving data aggregation scheme for smart grid,” in 2014 IEEE Global Communications Conference. IEEE, 2014, pp. 4720–4725.
D. He, N. Kumar, and J.-H. Lee, “Privacy-preserving data aggregation scheme against internal attackers in smart grids,” Wireless Networks, vol. 22, no. 2, pp. 491–502, 2016.
S. Li, K. Xue, Q. Yang, and P. Hong, “Ppma: Privacy-preserving multisubset data aggregation in smart grid,” IEEE Transactions on Industrial Informatics, vol. 14, no. 2, pp. 462–471, 2017.
D. Li, Z. Aung, J. R. Williams, and A. Sanchez, “Efficient authentication scheme for data aggregation in smart grid with fault tolerance and fault diagnosis,” in 2012 IEEE PES Innovative Smart Grid Technologies (ISGT). IEEE, 2012, pp. 1–8.
Z. Guan, G. Si, X. Zhang, L. Wu, N. Guizani, X. Du, and Y. Ma, “Privacy-preserving and efficient aggregation based on blockchain for power grid communications in smart communities,” IEEE Communications Magazine, vol. 56, no. 7, pp. 82–88, 2018.
I.-C. Lin and T.-C. Liao, “A survey of blockchain security issues and challenges.” IJ Network Security, vol. 19, no. 5, pp. 653–659, 2017.
F. Li and B. Luo, “Preserving data integrity for smart grid data aggregation,” in 2012 IEEE Third International Conference on Smart Grid Communications (SmartGridComm). IEEE, 2012, pp. 366–371.
F. Diao, F. Zhang, and X. Cheng, “A privacy-preserving smart metering scheme using linkable anonymous credential,” IEEE Transactions on Smart Grid, vol. 6, no. 1, pp. 461–467, 2014.
E. Vahedi, M. Bayat, M. R. Pakravan, and M. R. Aref, “A secure eccbased privacy preserving data aggregation scheme for smart grids,” Computer Networks, vol. 129, pp. 28–36, 2017.
R. Mahmud, R. Kotagiri, and R. Buyya, “Fog computing: A taxonomy, survey and future directions,” in Internet of everything. Springer, 2018, pp. 103–130.
L. Zhu, M. Li, Z. Zhang, C. Xu, R. Zhang, X. Du, and N. Guizani, “Privacy-preserving authentication and data aggregation for fog-based smart grid,” IEEE Communications Magazine, vol. 57, no. 6, pp. 80–85, 2019.
X. Liu, Y. Zhang, B. Wang, and H. Wang, “An anonymous data aggregation scheme for smart grid systems,” Security and communication networks, vol. 7, no. 3, pp. 602–610, 2014.
G. Ohtake, R. Safavi-Naini, and L. F. Zhang, “Outsourcing scheme of abe encryption secure against malicious adversary,” Computers & Security, vol. 86, pp. 437–452, 2019.
M. Badra and S. Zeadally, “Lightweight and efficient privacy preserving data aggregation approach for the smart grid,” Ad Hoc Networks, vol. 64, pp. 32–40, 2017.
L. Chen, R. Lu, and Z. Cao, “Pdaft: A privacy-preserving data aggregation scheme with fault tolerance for smart grid communications,” Peer-to-Peer networking and applications, vol. 8, no. 6, pp. 1122–1132, 2015.
V. Lozupone, “Analyze encryption and public key infrastructure (pki),” International Journal of Information Management, vol. 38, no. 1, pp. 42–44, 2018.
C. Varma, “A study of the ecc, rsa and the diffie-hellman algorithms in network security,” in 2018 International Conference on Current Trends towards Converging Technologies (ICCTCT), 2018, pp. 1–4.